Related Keywords
algorithm downloadsalgorithm 2 downloads
algorithm development downloads
algorithm optimization downloads
algorithm x64 downloads
md5 algorithm downloads
aes encryption algorithm downloads
optimization algorithm downloads
using aes algorithm downloads
sha 1 algorithm downloads
secure hash algorithm downloads
genetic algorithm downloads
compression algorithm downloads
genetic algorithm optimizatio downloads
reliable algorithm and all downloads
google algorithm downloads
image algorithm downloads
comparison algorithm downloads
encryption algorithm downloads
checksum algorithm downloads
Top Software Keywords
decrypt downloadsencryption downloads
aes downloads
encryption software downloads
safe downloads
file encryption downloads
privacy downloads
decryption downloads
data encryption downloads
secure downloads
password downloads
security downloads
folder lock downloads
files downloads
recovery downloads
encrypt downloads
protection downloads
file downloads
email downloads
protect downloads
folder downloads
crack downloads
hide downloads
folders downloads
blowfish downloads
lock downloads
lock folder downloads
recover downloads
rijndael downloads
des downloads
Vista Download
Vista downloadVista antivirus download
Vista wallpaper download
Vista wallpapers download
Vista themes download
Vista pack download
Vista ultimate download
Vista home download
Vista basic download
Vista business download
Vista x64 download
Vista transformation download
Vista transformation pack download
Vista boot download
Vista dvd download
Vista sidebar download
Vista aero download
Vista product key download
Top Downloads
Top Rated
Navigation: Home
\ Security & Privacy
\ Encryption Tools \ XorIt
XorIt1.9 by Sinner Computing |

|
Software Description:
Most file encryptors use methods that rely on the theory of computational security, that is difficulty of key factorisation prevents decryption of the file. But this method may not work forever. XorIt is designed to use conventional XOR encryption on keys that are the same size as the file to be encrypted. ...
Download XorItAdd to Download Basket Report virus or spyware |
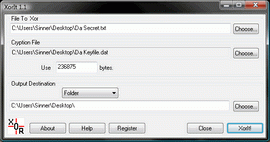 [ Zoom screenshot ] |
|
| Software Info | |
|
Best Vista Download periodically updates pricing and software information of XorIt full version from the publisher,
but some information may be out-of-date. You should confirm all information. Software piracy is theft, using crack, warez passwords, patches, serial numbers, registration codes, key generator, keymaker or keygen for XorIt license key is illegal and prevent future development of XorIt. Download links are directly from our mirrors or publisher's website, XorIt torrent files or shared files from rapidshare, yousendit or megaupload are not allowed! |
|
| Released: | October 22, 2022 |
| Filesize: | 33 kB |
| Language: | English |
| Platform: | Win2000, Windows 7 x32, Windows 7 x64, WinServer, Windows Vista, Windows Vista x64, Windows XP |
| Install | Install and Uninstall |
| Add Your Review or Windows Vista Compatibility Report |
XorIt- Releases History |
| Software: | XorIt 1.9 |
| Date Released: | Oct 22, 2022 |
| Status: | Minor Update |
| Release Notes: | Revised Xor-ing implementation and v1.9 rebuild |
| Software: | XorIt 1.1 |
| Date Released: | Dec 20, 2007 |
| Status: | Minor Update |
| Release Notes: | Internal revision, speed improvements, and interface changes. |
Most popular algorithm 2 in Encryption Tools downloads for Vista |
|
Rohos Disk Encryption 3.2 download by Tesline-Service.SRL
... encryption Rohos disk uses NIST approved AES encryption algorithm, 256 bit encryption key length. Encryption is automatic and on-the-fly. No risk of data loss Partition password reset option allows ...
View Details
Download
|
 |
|
Batch File Encrypt Free 5.0.125 download by BinaryMark
... using AES, Triple-DES (3DES), RC2, and DES symmetric algorithms. You can encrypt files with a single password or specify cryptographic keys (vectors) instead. You can change key bit length for ...
type: Shareware
View Details
Download
categories: batch, multiple, bulk, mass, files, encrypt, file encryption, decrypt, aes, 3-des, des, rc2, symmetric, algorithm, cryptographic, key, password, vector, bit strength |
 |
|
PenProtect 1.45 download by EasyLine
... using your Password and a special technique (AES algorithm 256 bit key). PenProtect requires no installation: it is a single file located in the home folder of your Flash Drive. ...
type: Demo ($19.00)
View Details
Download
categories: flash drive, USB, password, flash memory, pen drive, crypt, encrypt, decrypt, software, key, file, folder, AES, AES 256, security, cryptography, secure, stick, device, lock, guard flash drive, guard pen drive, penprotect |
 |
|
Digi-Shield (PC) 1.6 download by LC Technology International, Inc.
... important data using Rijndael, Twofish and Blowfish encryption algorithms. Once encrypted, even if the media is stolen ... adopted by the U.S. government. Rijndael is the algorithm that has been selected by the U.S. National ...
type: Demo ($39.95)
View Details
Download
categories: data security software, secure files, secure media, flash drives, encryption |
 |
|
abylon BASIC 23.60.1 download by abylonsoft - Dr. Thomas Klabunde
The protection of your sensitive data is often disregarded. But the encrypting of diaries, pictures or other secret documents with the AES- or Blowfish-Algorithm is relatively simple. With the help of ...
type: Shareware ($25.50)
View Details
Download
categories: sign, crypt, code, signing, coding, encryption, security, PKCS, plugin, utilitie, SME, digital envelop, encode, compress, zip, attachment, explorer, email, mapi, manager, cookies, history, WinCrypt, apm, abylon protection manager |
 |
|
BestCrypt Volume Encryption 5.12.3 download by Jetico Inc
... Encryption allows encrypting data with many strong encryption algorithms. Every algorithm is implemented with the largest possible key size defined in the algorithm's specification: * AES (Rijndael) - 256-bit key. * ...
type: Trialware ($99.95)
View Details
Download
categories: Volume Encryption, encryption algorithm, encryption key, Encryption, Encrypt, Encrypter |
 |
|
USB Flash Security 5.0.0 download by Kashu System Design Inc.
... recognized by speedy and cipher strength in encryption algorithm has been adopted. Data will be encrypted automatically ... recognized by speedy and cipher strength of encryption algorithm has been adopted. ...
type: Freeware
View Details
Download
categories: USB Flash Security, Encryption, Encrypt, AES256bit, Security tool, USB security, USB hard disk security, password |
 |
|
File Privacy 0.2 download by Vengito (alias Needed Special Tools)
... (3DES or TDES), officially the Triple Data Encryption Algorithm (TDEA or Triple DEA), is a symmetric-key block cipher, which applies the DES cipher algorithm three times to each data block. The Data ...
type: Commercial ($0.99)
View Details
Download
categories: File Privacy Encryption Decryption 3DES TDES Triple DES |
 |
|
abylon CRYPTDRIVE 23.60.1 download by abylonsoft - Dr. Thomas Klabunde
... create the software encrypted container, using the international algorithm standards AES and Blowfish with an key-length from 256 or 448 bit. An even greater protection offer the combination of these ...
type: Shareware ($38.00)
View Details
Download
categories: apm, Drive, abylon, abylonsoft, virtual drive, Partitials, Blowfish, AES, CRYPTDRIVE, SHAREDDRIVE, encryption, coding, RSA, PKCS, smart card, smardcard, Token, USB-Token, Certificate, HYBRID-System, SYMM-System, USB-stick, DVD, memory-stick |
 |
|
SecureCD Creator 2.0 download by KernSafe Technologies, Inc.
... SecureCD Creator use AES 256 and SHA256 bit algorithm, running at high security level. SecureCD Creator will give quadruple security for valuable data protection. Generally, SecureCD Creator can use for ...
type: Shareware ($34.90)
View Details
Download
categories: CD encryption, DVD Encryption, CD encrypt, DVD encrypt, CD password, DVD password, iso, iso9660, iso file, iso editor, iso edit, virtual CD-ROM, emulator, encrypt, encryption |