Related Keywords
sha 1 algorithm downloadssha downloads
sha 1 downloads
sha 512 downloads
sha 256 downloads
sha ocx downloads
sha hashes downloads
sha 160 downloads
sha 384 downloads
sha 224 downloads
sha password downloads
sha 2 downloads
sha 3 downloads
sha 3 256 downloads
sha 3 224 downloads
sha 3 384 downloads
sha 3 512 downloads
algorithm downloads
algorithm 2 downloads
algorithm development downloads
Top Software Keywords
picture gallery downloadsfreeware downloads
free proxy list downloads
irc proxy list downloads
free downloads
software downloads
real player downloads
windows downloads
internet downloads
mp3 downloads
winamp for vista downloads
video downloads
download downloads
crack downloads
file downloads
utility downloads
games downloads
vista downloads
tool downloads
vista key generator downloads
game downloads
screensaver downloads
password downloads
desktop downloads
security downloads
converter downloads
convert downloads
image downloads
fax software downloads
email downloads
Vista Download
Vista downloadVista antivirus download
Vista wallpaper download
Vista wallpapers download
Vista themes download
Vista pack download
Vista ultimate download
Vista home download
Vista basic download
Vista business download
Vista x64 download
Vista transformation download
Vista transformation pack download
Vista boot download
Vista dvd download
Vista sidebar download
Vista aero download
Vista product key download
Featured Download
Advanced
SystemCare
Speed up, repair &
clean PC system in
1 click

Smart Game
Booster
Free PC game
booster and
optimizer

RealPlayer
Media player for
web content
Top Downloads
Top Rated
| Displayed: 1 - 23 of 23 | |
| Sort by: relevance | title | downloads | rating | date | Show: All Software | Only Freeware |
|
LuJoSoft Checksum 1.0.0 download by LuJoSoft
Introduction: Description of MD5 The MD5 message-digest algorithm is a widely used cryptography hash function producing ... commonly used to verify data integrity. Description of SHA-1 SHA-1 (Secure Hash Algorithm 1) is a cryptographic ...
View Details
Download
|
 |
|
File Checksum Calculator 1.2 download by VOVSOFT
... that generates and verifies cryptographic hashes in MD5, SHA-1 and SHA-256. Cryptographic hash functions are commonly used to guard ... common cryptographic hash functions are the Secure Hash Algorithm (SHA) and Message Digest Algorithm-5 (MD5). Checksum utilities ...
View Details
Download
|
 |
|
File Checksum Utility 2.1.0.0 download by BLQ software
... software allows to generate MD (Message Digest) and SHA (Secure Hash Algorithm) hashes from a single file or files in ... value from the content of file by special algorithm. Duplicated files are highlighted, but also bigger and ...
type: Freeware
View Details
Download
categories: hash, SHA, checksum, MD5, Algorithm, integrity, archiving, duplicate, size, oldest |
 |
|
Free MD5 SHA1 Verifier 1.41 download by Keylack Software
... verify checksums (hash) of downloaded files. Supports MD5, SHA-1, HAVAL, MD2, SHA-256, SHA-384, SHA-512. Key Features: The program has a convenient user ... any file. Verify file checksum. Supports most hashing algorithm: MD5, SHA-1, HAVAL, MD2, SHA-256, SHA-384, SHA-512. Works ...
View Details
Download
|
 |
|
Toms Hash Explorer 1.2 download by Tom Andreas Mannerud
... verify file integrity. Supports the most popular hashing algorithms such as MD5, SHA-1, and SHA-2 including SHA256, SHA384, and SHA512. Key Features include: ... + Calculate Hash Values using industry standard hashing algorithms + Calculate File Entropy using Shannon's Entropy algorithm ...
type: Freeware
View Details
Download
categories: CRYPTO, HASH, HASHING, MD5, SHA, SHA-1, SHA-2, SHA256, SHA384, SHA512, SHANNON, ENTROPY, FILE INTEGRITY, FAST, MULTI-THREADED, FREE |
 |
|
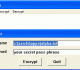
MarshallSoft dBase AES Library 5.0 download by MarshallSoft Computing
... National Institute of Standards and Technology (NIST).The AES algorithm is commonly used by many financial entities such ... - Supports ECB (Electronic Cookbook) mode. - Supports SHA-256 cryptographic hash algorithm. - Does random byte data ...
type: Shareware ($119.00)
View Details
Download
categories: AES encryption software, AES encryption, AES software, strong encryption, dBase software, security software, 256 bit encryption, encryption library, dBase encryption, dBase AES, Visual dBase AES |
 |
|
Md5deep 4.4 download by Jesse Kornblum
... is a set of programs to compute MD5, SHA-1, SHA-256, Tiger, or Whirlpool message digests on an arbitrary ... file matches a known file in one hash algorithm but not in others. The results are displayed ...
type: Freeware
View Details
Download
categories: compute MD5, compute SHA-1, recursive examine, compute, comparison, compare |
 |
|
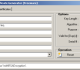
TekCERT 2.7.7 download by Yasin KAPLAN
... Generates 1024, 2048, 3072 and 4096 bits certificates. Sha-1withRSAEncryption, sha256withRSAEncryption, sha384withRSAEncryption and sha512withRSAEncryption key algorithms supported. Freeware version supports only sha-1withRSAEncryption. Supports Automatic Certificate Management Environment, ACME (RFC 8555), ...
View Details
Download
|
 |
|
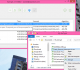
AxCrypt 2.1.1494 download by AxCrypt AB
... for Windows Vista or later using the AES algorithm with 256-bit or 128-bit keys. It combines strong symmetric encryption with compression and double-click editing/viewing. Encrypted files have a '.AXX' extension ...
type: Freeware
View Details
Download
categories: file, encryption, free, aes, shell extension, windows, encrypt, multiple backup, api, server, script, open source, gnu, gpl |
 |
|
abylon FREEHASH 2025.1 download by abylonsoft - Dr. Thomas Klabunde GbR
... The software supports a wide array of hashing algorithms, including MD5, SHA-1, and the more secure SHA-256, among others. This diversity in algorithm support ensures compatibility with various security standards and ...
type: Freeware
View Details
Download
categories: file integrity, abylon FREEHASH free download, checksum, software download, compare hash, SHA1, hash, Dr. Thomas Klabunde GbR, checksum generator, abylonsoft, MD5 hash, download abylon FREEHASH, hash generation, abylon FREEHASH, MD5 |
 |
|
Hash Codes 1.62.780.7200 download by Marek Sienczak
... supports: Adler32, CRC32, CRC64, MD2, MD4, MD5, MD6, SHA-0, SHA-1, SHA-1-IME, SHA-224, SHA-256, SHA-384, SHA-512, RIPEMD-128, RIPEMD-160, RIPEMD-256, RIPEMD-320 or Whirlpool algorithm. Features: Hash data from keyboard, file ... CRC32, CRC64, GOST, HAVAL, MD2, MD4, MD5, MD6, SHA-0, SHA-1, SHA-1-IME, SHA-224, SHA-256, SHA-384, SHA-512, RIPEMD-128, RIPEMD-160, ...
View Details
Download
|
 |
|
Hash Codes x64 1.62.780.7200 download by Marek Sienczak
... supports: Adler32, CRC32, CRC64, MD2, MD4, MD5, MD6, SHA-0, SHA-1, SHA-1-IME, SHA-224, SHA-256, SHA-384, SHA-512, RIPEMD-128, RIPEMD-160, RIPEMD-256, RIPEMD-320 or Whirlpool algorithm. Features: Hash data from keyboard, file ... CRC32, CRC64, GOST, HAVAL, MD2, MD4, MD5, MD6, SHA-0, SHA-1, SHA-1-IME, SHA-224, SHA-256, SHA-384, SHA-512, RIPEMD-128, RIPEMD-160, ...
type: Open Source
View Details
Download
categories: x64 hash data, x64 encrypt data, x64 data encryption, x64 hash, x64 encrypt, x64 encryption |
 |
|
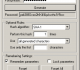
Cryptnos 1.3.3 download by Jeffrey T. Darlington
... and runs this data through a cryptographic hash algorithm to produce a password that is unique, lengthy, ... repeatable “passphrases” using a variety of cryptographic hash algorithms Supported hashing algorithms: MD5, SHA-1, SHA-256, SHA-384, SHA-512, ...
type: Open Source
View Details
Download
categories: password generator, generate password, cryptographic hash, password, generator, hash |
 |
|
MarshallSoft Visual Basic AES Library 6.0 download by MarshallSoft Computing
... National Institute of Standards and Technology (NIST).The AES algorithm is commonly used by many financial entities such ... - Supports ECB (Electronic Cookbook) mode. - Supports SHA-256 cryptographic hash algorithm. - Does random byte data ...
type: Shareware ($119.00)
View Details
Download
categories: AES encryption software, AES encryption, AES software, strong encryption, 256 bit encryption, encryption library, Visual Basic encryption, VB encryption, Visual Basic AES, VB AES, Visual Studio AES, VBA |
 |
|
MarshallSoft FoxPro AES Library 6.0 download by MarshallSoft Computing
... National Institute of Standards and Technology (NIST).The AES algorithm is commonly used by many financial entities such ... - Supports ECB (Electronic Cookbook) mode. - Supports SHA-256 cryptographic hash algorithm. - Does random byte data ...
type: Shareware ($119.00)
View Details
Download
categories: AES encryption software, AES encryption, AES software, strong encryption, FoxPro software, security software, 256 bit encryption, encryption library, FoxPro encryption, FoxPro AES, Visual FoxPro AES |
 |
|
MarshallSoft XBase++ AES Library 5.0 download by MarshallSoft Computing
... National Institute of Standards and Technology (NIST).The AES algorithm is commonly used by many financial entities such ... - Supports ECB (Electronic Cookbook) mode. - Supports SHA-256 cryptographic hash algorithm. - Does random byte data ...
type: Shareware ($119.00)
View Details
Download
categories: AES encryption software, AES encryption, AES software, strong encryption, xbase software, security software, 256 bit encryption, encryption library, xbase encryption, xbase++ encryption, xbase AES, xbase++ AES |
 |
|
MarshallSoft Delphi AES Library 6.0 download by MarshallSoft Computing
... National Institute of Standards and Technology (NIST).The AES algorithm is commonly used by many financial entities such ... - Supports ECB (Electronic Cookbook) mode. - Supports SHA-256 cryptographic hash algorithm. - Does random byte data ...
type: Shareware ($119.00)
View Details
Download
categories: AES encryption software, AES encryption, AES software, strong encryption, Delphi software, security software, 256 bit encryption, encryption library, Delphi encryption, Delphi AES |
 |
|
Appnimi SHA256 Decrypter 3.8.6 download by Appnimi
... Above all it is FREE. The Secure Hash Algorithm is one of a number of cryptographic hash ... signature for a text or a data file. SHA-256 algorithm generates an almost-unique, fixed size 256-bit hash. ...
View Details
Download
|
 |
|
Hexplorer 2.6 download by Sourceforge
... find repeating patterns in data, includes Fourier transform algorithm * Pixel viewer to show binaries as bitmaps ... and vice versa * Very fast Boyer-Moore find algorithm * Highlights selected byte strings in data to ...
type: Open Source
View Details
Download
categories: interpret bytes, hexadecimal editor, pixel viewer, pixel, viewer, hexadecimal |
 |
|
Python Encryption Library x64 9.5.0.98 download by Chilkat Software, Inc.
... binary data. Python Encryption Library implements symmetric encryption algorithms: Rijndael, Blowfish, Twofish. Also provides public-key encryption and ... RC2, ARC4, DES, 3DES, PBES1, PBES2. * Hash Algorithms: SHA-1, SHA256, SHA384, SHA512, MD2, MD4, MD5, HAVAL. ...
type: Trialware ($149.00)
View Details
Download
categories: x64 Python Encryption Library, x64 encrypt binary data, x64 decrypt strings, x64 strings, binary, x64 decrypt |
 |
|
Python Encryption Library 9.5.0.98 download by Chilkat Software, Inc.
... binary data. Python Encryption Library implements symmetric encryption algorithms: Rijndael, Blowfish, Twofish. Also provides public-key encryption and ... RC2, ARC4, DES, 3DES, PBES1, PBES2. * Hash Algorithms: SHA-1, SHA256, SHA384, SHA512, MD2, MD4, MD5, HAVAL. ...
type: Trialware ($149.00)
View Details
Download
categories: Python Encryption Library, encrypt binary data, decrypt strings, strings, binary, decrypt |
 |
|
MarshallSoft C/C++ AES Library 6.0 download by MarshallSoft Computing
... - Supports ECB (Electronic Cookbook) mode. - Supports SHA-256 cryptographic hash algorithm. - Does random byte data generation. - Allows ...
type: Shareware ($119.00)
View Details
Download
categories: AES encryption software, AES encryption, AES software, strong encryption, C/C++ software, security software, 256 bit encryption, encryption library, C/C++ encryption, C encryption, C++ encryption, C/C++ AES, C AES, C++ AES, Diffie-Hellman |
 |
|
TekOTP 1.4.2 download by KaplanSoft
... for updates. Generates OTPs with MD4, MD5 and SHA-1. Simple, easy to use GUI. Enter seed, pass phrase, set count and algorithm and click 'Calculate' button to generate an OTP.
View Details
Download
|
 |
| Displayed: 1 - 23 of 23 | |
| Sort by: relevance | title | downloads | rating | date | Show: All Software | Only Freeware |
| Copyright Notice | |
| Software piracy is theft, using crack, warez passwords, patches, serial numbers, registration codes, key generator, keymaker or keygen for license key is illegal. The above sha 1 algorithm search results are freeware or software in full, demo and trial versions for free download. Download links are directly from our mirrors or publisher's website, sha 1 algorithm torrent files or shared files from rapidshare, yousendit or megaupload are not allowed! |