Related Keywords
uses downloadsuses the standard ocl downloads
uses of student identity card downloads
uses of 2 of 5 barcodes downloads
list of possible uses downloads
salvia uses downloads
who uses offsite backup downloads
Top Software Keywords
free downloadsclean downloads
hide downloads
erase downloads
delete downloads
file downloads
keylogger downloads
crack downloads
wipe downloads
password downloads
remove downloads
security downloads
history downloads
cookies downloads
secure downloads
privacy downloads
protect downloads
internet downloads
recover downloads
cleaner downloads
shredder downloads
windows downloads
cache downloads
password recovery downloads
recovery downloads
lost password downloads
stealth downloads
utility downloads
kazaa downloads
freeraser downloads
Vista Download
Vista downloadVista antivirus download
Vista wallpaper download
Vista wallpapers download
Vista themes download
Vista pack download
Vista ultimate download
Vista home download
Vista basic download
Vista business download
Vista x64 download
Vista transformation download
Vista transformation pack download
Vista boot download
Vista dvd download
Vista sidebar download
Vista aero download
Vista product key download
Top Downloads
Top Rated
Navigation: Home
\ Security & Privacy
\ Other \ Webroot SecureAnywhere Complete
Webroot SecureAnywhere Complete2013 8.0.2.174 by Webroot Software |

|
Software Description:
Webroot SecureAnywhere Complete uses a radically new cloud-based approach to online security that protects you against the latest threats as soon as they emerge. And it does so at blazing fast speeds, scanning your entire PC in about 2 minutes. (After the initial scan of your PC, full system scans will typically take two minutes or less.)Webroot SecureAnywhere Complete also backs up your files and blocks dangerous web links. ... Download Webroot SecureAnywhere Complete Add to Download Basket Report virus or spyware |
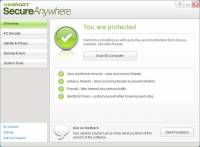 [ Zoom screenshot ] |
|
| Software Info | |
|
Best Vista Download periodically updates pricing and software information of Webroot SecureAnywhere Complete full version from the publisher,
but some information may be out-of-date. You should confirm all information. Software piracy is theft, using crack, warez passwords, patches, serial numbers, registration codes, key generator, keymaker or keygen for Webroot SecureAnywhere Complete license key is illegal and prevent future development of Webroot SecureAnywhere Complete. Download links are directly from our mirrors or publisher's website, Webroot SecureAnywhere Complete torrent files or shared files from rapidshare, yousendit or megaupload are not allowed! |
|
| Released: | August 28, 2013 |
| Filesize: | 666 kB |
| Platform: | Windows XP, Windows Vista, Windows Vista x64, Windows 7, Windows 7 x64 |
| Install | Instal And Uninstall |
| Add Your Review or Windows Vista Compatibility Report |
Webroot SecureAnywhere Complete- Releases History |
| Software: | Webroot SecureAnywhere Complete 2013 8.0.2.1 |
| Date Released: | Aug 28, 2013 |
| Status: | New Release |
| Release Notes: | · Potentially dropping the first keystroke on localized platforms. · A crash when prompting for an email address on installation on localized OSs. · Compatibility with Google Chrome’s nacl64.exe. · General RealTime Shield functionality · Compatibility with the new version of ExploitShield, now part of MalwareBytes. |
| Software: | Webroot SecureAnywhere Complete 2013 8.0.2.1 |
| Date Released: | Aug 8, 2013 |
| Status: | New Release |
| Release Notes: | Fixed: · Potentially dropping the first keystroke on localized platforms. · A crash when prompting for an email address on installation on localized OSs. · Compatibility with Google Chrome’s nacl64.exe. · General RealTime Shield functionality · Compatibility with the new version of ExploitShield, now part of MalwareBytes. |
| Software: | Webroot SecureAnywhere Complete 2013 8.0.2.1 |
| Date Released: | Jun 20, 2013 |
| Status: | New Release |
| Release Notes: | Improved: · Performance when installed alongside Citrix environments. Added: · Central management for controlling System Cleaner settings and controls in the online management console. · Heuristics to detect a new AutoCAD virus. Fixed: · Compatibility issues with proxy settings during and after installation. · Incompatibility with ESET’s self-protection on Windows 8. · Processing detection configuration option when program launches. · EICAR is now submitted as an executable file to be displayed within the console. |
Most popular uses in Other downloads for Vista |
|
Romaco Timeout 3.1.4.0 download by Mark Furneaux
... amount of time that a child (or anyone) uses their computer for. It can also restrict Internet usage time, or create a window of time in which the computer can ...
type: Freeware
View Details
Download
categories: Time restriction, Computer lockdown, Restrict usage, Restriction, Restrict, Lockdown |
 |
|
Webroot SecureAnywhere Complete 2013 8.0.2.174 download by Webroot Software
... tablet and mobile protection Webroot SecureAnywhere Complete uses a radically new cloud-based approach to online security ... real-time protection -Blazing Fast Performance, Exceptional Value Uses minimal memory and processor capacity Won't disrupt your ...
View Details
Download
|
 |
|
LocK-A-FoLdeR 64-bit 3.10.3 download by Gurjit Singh
... easy to use and straightforward Interface. Uses almost no CPU (no extra services or processes). Compatible with Windows XP/Vista/7. Open Source (Free To Use/Distribute/Study/Modify). ...
type: Open Source
View Details
Download
categories: folder lockdown x64, protect folder x64, lock directory x64, lockdown x64, lock x64, password x64 |
 |
|
Prey x64 1.12.9 download by Fork Ltd.
... Key features 100% geolocation aware Prey uses either the device's GPS or the nearest WiFi hotspots to triangulate and grab a fix on its location. It's shockingly accurate. ...
type: Open Source
View Details
Download
categories: control, security, protect, remote, Laptop Tracker, Locate Computer, Secure Laptop, x64 |
 |
|
Process Heap Viewer 4.5 download by SecurityXploded
... quickly enumerate Process Heap memory on Windows. It uses much smarter technique than slower Windows heap API functions. This makes it one of the fastest tool for quickly enumerating thousands ...
type: Freeware
View Details
Download
categories: procheapviewer, process heap, scan process heap, heap scanner, fast heap viewer, process memory |
 |
|
Webroot SecureAnywhere Internet Security Plus 2013 8.0.2.174 download by Webroot Software
... threats Most scans take less than two minutes* Uses less computer memory than competitive security products ...
type: Trialware ($59.99)
View Details
Download
categories: Internet security, malware cleaner, clean virus, malware, cleaner, firewall |
 |
|
AVG Family Safety 2012.715 download by Grisoft
... cyber bullying or grooming. AVG Family Safety® uses key-stroke technology to monitor your child's activities in chat-rooms and on social networking sites. If it spots words, phrases or language ...
View Details
Download
|
 |
|
Mil Free Internet Eraser 4.0 download by Mil Incorporated
Mil Free Internet Eraser is an application designed to protect your privacy. Most people do not know that a lot of information is saved by their computer about what web sites ...
type: Freeware
View Details
Download
categories: free internet eraser, delete, clean, erase history, cookies, index.dat files, online privacy, Mil Shield, Mil Incorporated |
 |
|
Data Destroyer 17.07 download by Hermetic Systems
... data will remain there until the operating system uses those sectors when writing new data. Until the old data is overwritten (which take months or longer) it can be recovered ...
type: Shareware ($27.95)
View Details
Download
categories: data destroyer, disk, purge, file purge, secure deletion, secure file deletion, sanitize, sanitization, DoD, Defense, 5220.22-M, file deletion |
 |
|
i-Catcher Console 6.3 B3 download by iCode Systems Ltd.
... a modern digital CCTV system. i-Catcher Console uses a wide range of camera devices, including USB ... We have set up a web page that uses our Console with an Axis 241Q video server ...
type: Trialware ($237.00)
View Details
Download
categories: video surveillance, surveillance record, network camera, surveillance, camera, webcam |
 |