Related Keywords
text using downloadspaste text using hotkey downloads
paste text using hotkeys downloads
using the text to speech tool downloads
text messaging software using usb modem downloads
using vb downloads
using downloads
using keyword downloads
using aes algorithm downloads
using robocopy downloads
using guest book downloads
using wizard to create a new downloads
using cards you downloads
using affiliate creator will downloads
using a visual downloads
using rudraksh downloads
using csv splitters downloads
using english dictionary downloads
using notes in outlook downloads
using batch downloads
Top Software Keywords
decrypt downloadsencryption downloads
aes downloads
safe downloads
encryption software downloads
file encryption downloads
decryption downloads
privacy downloads
data encryption downloads
secure downloads
folder lock downloads
password downloads
security downloads
files downloads
recovery downloads
encrypt downloads
protection downloads
file downloads
email downloads
folder downloads
protect downloads
crack downloads
hide downloads
blowfish downloads
folders downloads
lock downloads
lock folder downloads
recover downloads
rijndael downloads
des downloads
Vista Download
Vista downloadVista antivirus download
Vista wallpaper download
Vista wallpapers download
Vista themes download
Vista pack download
Vista ultimate download
Vista home download
Vista basic download
Vista business download
Vista x64 download
Vista transformation download
Vista transformation pack download
Vista boot download
Vista dvd download
Vista sidebar download
Vista aero download
Vista product key download
Top Downloads
Top Rated
Navigation: Home
\ Security & Privacy
\ Encryption Tools \ Toms Hash Explorer
Toms Hash Explorer1.2 by Tom Andreas Mannerud |

|
Software Description:
Toms Hash Explorer is a fast multi-threaded cryptographic hash calculation suite with an innovative Explorer-like user interface. This free Windows utility allows you to easily calculate cryptographic hash values for single files or entire folders to verify file integrity. Supports the most popular hashing algorithms such as MD5, SHA-1, and SHA-2 including SHA256, SHA384, and SHA512. ...
type: Freeware
Download Toms Hash Explorercategories: CRYPTO, HASH, HASHING, MD5, SHA, SHA-1, SHA-2, SHA256, SHA384, SHA512, SHANNON, ENTROPY, FILE INTEGRITY, FAST, MULTI-THREADED, FREE Add to Download Basket Report virus or spyware |
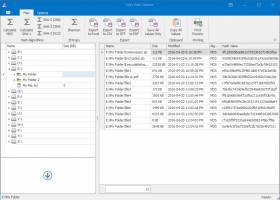 [ Zoom screenshot ] |
|
| Software Info | |
|
Best Vista Download periodically updates pricing and software information of Toms Hash Explorer full version from the publisher,
but some information may be out-of-date. You should confirm all information. Software piracy is theft, using crack, warez passwords, patches, serial numbers, registration codes, key generator, keymaker or keygen for Toms Hash Explorer license key is illegal and prevent future development of Toms Hash Explorer. Download links are directly from our mirrors or publisher's website, Toms Hash Explorer torrent files or shared files from rapidshare, yousendit or megaupload are not allowed! |
|
| Released: | August 20, 2016 |
| Filesize: | 17.44 MB |
| Language: | English |
| Platform: | Win2000, Windows XP, Windows 7 x32, Windows 7 x64, Windows 8, Windows 10, WinServer, WinOther, Windows Vista, Windows Vista x64 |
| Requirements: | Microsoft .NET Framework 4.5.2 |
| Install | Install and Uninstall |
| Add Your Review or Windows Vista Compatibility Report |
Toms Hash Explorer- Releases History |
| Software: | Toms Hash Explorer 1.2 |
| Date Released: | Aug 20, 2016 |
| Status: | Minor Update |
| Release Notes: | File Integrity Verification/Batch Verification |
| Software: | Toms Hash Explorer 1.1 |
| Date Released: | Apr 29, 2016 |
| Status: | New Release |
| Release Notes: | Themes/Skin Support, Drag and Drop, and File Entropy Computation using Shannon's Entropy Algorithm. |
Most popular text using in Encryption Tools downloads for Vista |
|
DataSafe 5.1 download by Cascade Research
... the disk througput rather than by CPU cycles. Using DataSafe With the mouse select All Programs -> ... the right. Click on a file and a text indicating if the file has been encrypted or ...
View Details
Download
|
 |
|
Paranoia Text Encryption for PC 15.0.4 download by Paranoia Works
... SMS, ...), cryptocurrency keys (seeds, mnemonics), and other texts safe from all unwanted readers. Texts are encrypted using strong encryption algorithms: AES (Rijndael) 256bits, RC6 256bit, ... available. A steganography implementation is included (concealing a text within an image - JPG). A steganographic algorithm ...
type: Freeware
View Details
Download
categories: encryption, encrypter, encryptor, encrypt, note, notes, text, texts, messages, chat, email, emails, sms, social, ciphering, encipher, aes, blowfish, threefish, serpent, 256, 512, 1024, bit, bits, steganography, JPG, cryptocurrency, seed, mnemonic, key, keys, safe, vault, password |
 |
|
Toms Hash Explorer 1.2 download by Tom Andreas Mannerud
... + Multi-threaded computation engine + Calculate Hash Values using industry standard hashing algorithms + Calculate File Entropy using Shannon's Entropy algorithm + Drag and Drop (Single ... +Print Full Results + Save Hash Values to Text File or Copy to Clipboard for easy import ...
type: Freeware
View Details
Download
categories: CRYPTO, HASH, HASHING, MD5, SHA, SHA-1, SHA-2, SHA256, SHA384, SHA512, SHANNON, ENTROPY, FILE INTEGRITY, FAST, MULTI-THREADED, FREE |
 |
|
Protected Storage viewer 2.8 download by Scalabium Software
... You may get/recovery this information without any problem using our viewer - MSN Explorer: you may recovery the sign-up passwords You may save the data as CSV/text file. ...
type: Shareware ($15.00)
View Details
Download
categories: Protected Storage, AutoComplete, password, stored, recover, reveal, crack, login, logon, password recovery, show password, show hidden password, view hidden password, password show, hidden password, see hidden passwords, showpassword, password, hidden, show, asterisk, showpw, showpassword |
 |
|
ZXI Decrypter 1.0.0.0 download by Afaan Bilal
... decrypt the messages that have been protected by using the ZXI Encrypter. In order to decode a ... the pass code and to paste the encrypted text in the main window of the application. ...
type: Freeware
View Details
Download
categories: remove protection, decrypt text message, message decryption, decrypt, decryption, remove |
 |
|
UserAssistView 1.02 download by NirSoft
... can save the list of UserAssist entries into text/html/xml/csv file, as well as you can delete unwanted items. Using UserAssistView UserAssistView doesn't require any installation process or additional DLL files. In order to start using it, simply run the executable file - UserAssistView.exe ...
View Details
Download
|
 |
|
Advanced Encryption Package 2015 Professional 6.01 download by SecureAction Research LLC
... your sensitive documents (20 encryption algorithms). File and/or text encryption. Symmetric and asymmetric algorithms (17 data destruction algorithms). Secure file deletion. Using USB flash drives to store [en]-decryption keys. Creating
type: Trialware ($49.95)
View Details
Download
categories: encrypt file, file ecryption, file shredder, encrypt, decrypt, encryptor |
 |
|
IMProcessor 3.5 download by Bigboot Software
... encrypting data typically produces chunks of illegible scrambled text, which can alert 3rd parties to the fact ... ownership of an image, by embedding a unique text file with owner details within the image or ...
type: Demo ($45.00)
View Details
Download
categories: Steganography, image, files, software, encrypted, encryption, Improcessor, hidden, backup |
 |
|
Confidential Free Edition 1.0 download by Eagle-Soft
... It allows you to hide an image and/or text within a visible image. Confidential uses the AES-256 ... whether for groups or individuals. Some possibilities of using Confidential among many others: Confidential communication. Blog out ...
View Details
Download
|
 |
|
Advanced File Cypher made easy 2.0.2 download by James Enterprises of NY, Inc.
... or use the file without first decrypting it using Advanced File Cypher (made easy) and the correct encryption keys. With Advanced File Cypher (made easy) sending important files or picture ...
type: Shareware ($19.95)
View Details
Download
categories: file encryption, text encryption, cypher, cipher, encryption, james enterprises of ny, james enterprises, free software. |
 |