Related Keywords
targeted downloadstargeted traffic downloads
targeted email downloads
targeted addresses downloads
targeted mailing lists downloads
targeted web site traffic downloads
targeted visitors downloads
targeted website spider downloads
targeted resumes downloads
targeted descent downloads
targeted email marketing downloads
targeted website traffic downloads
targeted campaign downloads
targeted mlm leads downloads
targeted emails downloads
targeted mailing list downloads
targeted business mailing list downloads
targeted list downloads
targeted leads downloads
targeted searc downloads
Top Software Keywords
virus protection downloadsfirewall downloads
adware downloads
antivirus downloads
trojan downloads
vista antivirus downloads
anti downloads
malware downloads
removal downloads
protection downloads
worm downloads
security downloads
scan downloads
worms downloads
free downloads
anti virus downloads
scanner downloads
internet security downloads
anti spyware downloads
virus downloads
trojans downloads
spyware downloads
blocker downloads
online security downloads
anti virus tools downloads
phishing downloads
spam downloads
virus removers downloads
online privacy downloads
virus checker downloads
Vista Download
Vista downloadVista antivirus download
Vista wallpaper download
Vista wallpapers download
Vista themes download
Vista pack download
Vista ultimate download
Vista home download
Vista basic download
Vista business download
Vista x64 download
Vista transformation download
Vista transformation pack download
Vista boot download
Vista dvd download
Vista sidebar download
Vista aero download
Vista product key download
Top Downloads
Top Rated
Navigation: Home
\ Security & Privacy
\ Anti-Virus Tools \ Symantec Endpoint Protection
Symantec Endpoint Protection14.3.3384.1000 by Symantec |

|
Software Description:
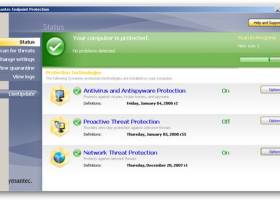
Symantec Endpoint Protection is built on multiple layers of protection, including Symantec Insight and SONAR both of which provide protection against new and unknown threats. Built for virtual environments, it can integrate with VMware vShield Endpoint for dramatically improved performance. ...
type: Trialware ($54.18)
Download Symantec Endpoint Protectioncategories: Virus Protection, Malware Protection, Rootkit Detection, Antivirus, Protection, Rootkit Add to Download Basket Report virus or spyware |
 [ Zoom screenshot ] |
|
| Software Info | |
|
Best Vista Download periodically updates pricing and software information of Symantec Endpoint Protection full version from the publisher,
but some information may be out-of-date. You should confirm all information. Software piracy is theft, using crack, warez passwords, patches, serial numbers, registration codes, key generator, keymaker or keygen for Symantec Endpoint Protection license key is illegal and prevent future development of Symantec Endpoint Protection. Download links are directly from our mirrors or publisher's website, Symantec Endpoint Protection torrent files or shared files from rapidshare, yousendit or megaupload are not allowed! |
|
| Released: | December 05, 2020 |
| Filesize: | 1900.00 MB |
| Platform: | Windows XP, Windows Vista, Windows Vista x64, Windows 7, Windows 7 x64, Windows 8, Windows 8 x64, Windows 10, Windows 10 x64 |
| Install | Instal And Uninstall |
| Add Your Review or Windows Vista Compatibility Report |
Symantec Endpoint Protection- Releases History |
| Software: | Symantec Endpoint Protection 14.3.3384.10 |
| Date Released: | Dec 5, 2020 |
| Status: | New Release |
| Release Notes: | Protection Features: Includes the new Symantec Mac Agent and the Symantec Linux Agent that can be installed and managed from either the on-premises Symantec Endpoint Protection Manager or the Integrated Cyber Defense Manager cloud console. Installing the Symantec Endpoint Protection client for Mac Installing the Symantec Agent for Linux 14.3 RU1 Prevents new and unknown threats on the macOS by monitoring nearly 1,400 file behaviors in real time. The new Mac Agent includes these behavioral protection capabilities. Behavioral protection, or SONAR, uses artificial intelligence and advanced machine learning for zero-day protection to effectively stop new threats. Managing SONAR Blocks untrusted non-portable executable (PE) files such as PDF files and scripts that are not yet identified as a threat. In the Exceptions policy, click Windows Exceptions. |
Most popular targeted in Anti-Virus Tools downloads for Vista |
|
Trend Micro HouseCall 1.62.1.1162 download by Trend Micro
... (new in 7.1). * Quick scan option offers targeted scanning of critical system areas and active threats, reducing scan times to within a few minutes. * Stand-alone, browser-independent implementation eliminates ...
type: Freeware
View Details
Download
categories: scanner, virus, Trojan, worm, malware, antivirus, remove, clean malware, protection |
 |
|
Trend Micro HouseCall 64bit 1.62.1.1162 download by Trend Micro
... (new in 7.1). * Quick scan option offers targeted scanning of critical system areas and active threats, reducing scan times to within a few minutes. * Stand-alone, browser-independent implementation eliminates ...
type: Freeware
View Details
Download
categories: scanner x64, virus x64, Trojan x64, worm x64, malware x64, antivirus x64, remove x64 |
 |
|
Panda Antivirus for Netbooks 9.01 download by Panda Security
... PC. This last line of defence blocks zero-day targeted attacks and terminates any malicious activity that has evaded traditional protection systems. Personal Firewall Protects you against Internet-borne worms ...
View Details
Download
|
 |
|
Symantec Endpoint Protection 14.3.3384.1000 download by Symantec
... sophisticated protection from large-scale malware to the most targeted attacks. Only Symantec uses Insight, with the collective wisdom of 200+ million systems in over 200 countries to identify and create ...
type: Trialware ($54.18)
View Details
Download
categories: Virus Protection, Malware Protection, Rootkit Detection, Antivirus, Protection, Rootkit |
 |
|
Dr.Web Katana 1.0.20.11260 download by Doctor Web
... offering preventive protection against the latest active threats, targeted attacks, and attempts by Trojans and exploits to use vulnerabilities, including zero-day ones, to penetrate systems, that is unknown to your ...
View Details
Download
|
 |