Related Keywords
suspicious file downloadssuspicious content downloads
suspicious downloads
suspicious network activity downloads
file properties changer creation date last access date last modification date file attributes file name extension downloads
file search file finder downloads
file to file downloads
file in file downloads
file rename change file name downloads
file folders multiple file folders downloads
file downloads
file transfer downloads
file attribute downloads
file tools downloads
file time downloads
file management downloads
file attributes downloads
file encryption downloads
file manager downloads
file backup software downloads
Top Software Keywords
free downloadsclean downloads
hide downloads
file downloads
erase downloads
delete downloads
keylogger downloads
security downloads
crack downloads
password downloads
wipe downloads
remove downloads
history downloads
cookies downloads
secure downloads
privacy downloads
protect downloads
cleaner downloads
internet downloads
recover downloads
windows downloads
shredder downloads
cache downloads
recovery downloads
password recovery downloads
lost password downloads
stealth downloads
utility downloads
kazaa downloads
freeraser downloads
Vista Download
Vista downloadVista antivirus download
Vista wallpaper download
Vista wallpapers download
Vista themes download
Vista pack download
Vista ultimate download
Vista home download
Vista basic download
Vista business download
Vista x64 download
Vista transformation download
Vista transformation pack download
Vista boot download
Vista dvd download
Vista sidebar download
Vista aero download
Vista product key download
Top Downloads
Top Rated
Navigation: Home
\ Security & Privacy
\ Other \ Autorun Eater
Autorun Eater2.6 by Old McDonald’s Farm |

|
Software Description:
... is infected with a malware and an 'autorun.inf' file is dropped, the shell menu is normally modified to execute the malware whenever the unsuspecting user double-clicks the infected drive. ...
Download Autorun EaterAdd to Download Basket Report virus or spyware |
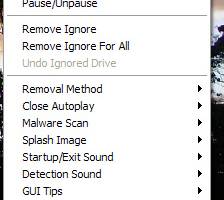 [ Zoom screenshot ] |
|
| Software Info | |
|
Best Vista Download periodically updates pricing and software information of Autorun Eater full version from the publisher,
but some information may be out-of-date. You should confirm all information. Software piracy is theft, using crack, warez passwords, patches, serial numbers, registration codes, key generator, keymaker or keygen for Autorun Eater license key is illegal and prevent future development of Autorun Eater. Download links are directly from our mirrors or publisher's website, Autorun Eater torrent files or shared files from rapidshare, yousendit or megaupload are not allowed! |
|
| Released: | October 22, 2013 |
| Filesize: | 1.40 MB |
| Platform: | Windows XP, Windows Vista, Windows Vista x64, Windows 7, Windows 7 x64, Windows 8, Windows 8 x64, Windows 10, Windows 10 x64 |
| Install | Instal And Uninstall |
| Add Your Review or Windows Vista Compatibility Report |
Autorun Eater- Releases History |
| Software: | Autorun Eater 2.6 |
| Date Released: | Oct 22, 2013 |
| Status: | New Release |
| Release Notes: | Added: ‘Malware Scan’ option to scan the infected storage device using Microsoft Security Essentials’ command line scanner (only works with version 2.1.1116.0 and above) after removing the suspicious ‘autorun.inf’ file. Added: ‘MSE Scan Log’ option to view the Microsoft Security Essentials scan log. |
Most popular suspicious file in Other downloads for Vista |
|
Crypt-O 3.4.433 download by Soft-o
... an organization. With Crypt-O, you can share encrypted files and folders seamlessly, ensuring that sensitive information remains ... and accountability. Detailed logs help in identifying any suspicious activities and ensure compliance with regulatory requirements. ...
type: Trialware
View Details
Download
categories: Crypt-O, download Crypt-O, Crypt-O free download, create database, database manager, encrypt database, encrypt, secure, manager, organizer |
 |
|
McAfee Identity Protection download by Mcafee
... 3 Bureau Credit Monitoring Monitors your credit file across all bureaus (Experian, Equifax and Transunion) and ... Protection sends you email and SMS-text alerts if suspicious activity is detected by our 24x7x365 scans of ...
type: Trialware ($9.99)
View Details
Download
categories: detection, encryption, McAfee, antivirus protection, monitoring, Secure |
 |
|
loginTimer 9.3.8.23 download by Satheesh.S
... stores them for you in a private text file, in addition to all users' login date, time, ... continuously, one by one, in a private log file. This makes it easy for you to identify ...
type: Demo ($400.00)
View Details
Download
categories: Y2K, Y2K38, Year 2038, Windows login, logintimer, satheeshsoft, discovery, inventions, invention, technology invention, technology discovery, computer login date time number of login, 2038, y2k y2k38 technology invented software, y2k38 invention |
 |
|
GetSusp 4.1.0.139 download by Mcafee
... and querying the McAfee Global Threat Intelligence (GTI) file reputation database to gather suspicious files. GetSusp is recommended as a first tool ... follow the existing McAfee support process for escalating suspicious files it finds. ...
type: Freeware
View Details
Download
categories: McAfee tool, malware detector, analyze malware, McAfee, malware, detector |
 |
|
RogueKiller 64-bit 14.8.5.0 download by Adlice Software
... scans all your currently active processes and terminates suspicious ones, in order to free up some memory. ... mode automatically starts at initialization and kills any suspicious processes. The file list shows the status, type, ...
type: Freeware
View Details
Download
categories: scan process x64, registry cleaner x64, x64 registry, process scanner x64, scan x64, scanner x64, cleaner x64 |
 |
|
CryptoPrevent 9.1.0.0 download by Foolish IT
... by securing the most vital locations of your file system against any type of modification. In addition, ... the Cryptolocker malware or ‘ransomware’, which encrypts personal files and then offers decryption for a paid ransom. ...
type: Freeware
View Details
Download
categories: CryptoLocker blocker, block CryptoLocker, CryptoLocker removal, CryptoLocker, removal, cleaner, block |
 |
|
Action1 Network Activity Monitor 2.6 download by Action1 Corporation
... or IIS running? - List of endpoints exposing file shares to ransomware. - Show endpoints with remote ... any of your endpoints. - Users storing sensitive files locally on unsecured laptops. - Systems at risk ...
type: Freeware
View Details
Download
categories: network activity monitoring software, network traffic monitoring, suspicious network activity, open file shares, open ports |
 |
|
SurveilStar Professional 1.2.4 download by SurveilStar Inc.
... screenshots, emails, IM chats, websites, used programs and files, etc. but also allows you to restrain users' ... Like MSN, ICQ, Skype, GTalk, etc. · Control Suspicious IM File Transfer · Backup Files Sent via ...
type: Trialware ($29.95)
View Details
Download
categories: employee monitor, monitor activity, PC monitor, monitor, surveillance, keylogger |
 |
|
Webroot SecureAnywhere Complete 2013 8.0.2.174 download by Webroot Software
... portal to manage your PC and mobile security, file backups, and passwords. Lightning-fast scans immediately detect security ... and mobile protection stops unknown threats based on suspicious behavior Online security continually updates itself so it's ...
View Details
Download
|
 |
|
FT 4.0 download by FayeTRACKER
... the Internet. These applications can include web browsers, file downloading utilities, communication applications and so on. Some ... and turns yellow and red if there are suspicious applications. Using a single click, the user ...
type: Freeware
View Details
Download
categories: track connection, connection detector, detect application, detector, detect, connection |
 |