Related Keywords
single user downloadssingle user license downloads
single user mode downloads
single user and other licensing options a downloads
gb single user downloads
pos single user downloads
included superzip single user downloads
single dvd downloads
single sign on downloads
single downloads
single deck downloads
single player downloads
single linked lists downloads
single table tournament downloads
single click sign on downloads
single source downloads
single click downloads
single point of access downloads
single currency downloads
single company downloads
Top Software Keywords
decrypt downloadsencryption downloads
aes downloads
safe downloads
encryption software downloads
file encryption downloads
decryption downloads
data encryption downloads
privacy downloads
secure downloads
folder lock downloads
password downloads
security downloads
files downloads
recovery downloads
encrypt downloads
protection downloads
file downloads
email downloads
folder downloads
protect downloads
crack downloads
hide downloads
blowfish downloads
folders downloads
lock downloads
lock folder downloads
recover downloads
rijndael downloads
des downloads
Vista Download
Vista downloadVista antivirus download
Vista wallpaper download
Vista wallpapers download
Vista themes download
Vista pack download
Vista ultimate download
Vista home download
Vista basic download
Vista business download
Vista x64 download
Vista transformation download
Vista transformation pack download
Vista boot download
Vista dvd download
Vista sidebar download
Vista aero download
Vista product key download
Top Downloads
Top Rated
Navigation: Home
\ Security & Privacy
\ Encryption Tools \ Toms Hash Explorer
Toms Hash Explorer1.2 by Tom Andreas Mannerud |

|
Software Description:
... cryptographic hash calculation suite with an innovative Explorer-like user interface. This free Windows utility allows you to easily calculate cryptographic hash values for single files or entire folders to verify file integrity. Supports the most popular hashing algorithms such as MD5, SHA-1, and SHA-2 including SHA256, SHA384, and SHA512. ...
type: Freeware
Download Toms Hash Explorercategories: CRYPTO, HASH, HASHING, MD5, SHA, SHA-1, SHA-2, SHA256, SHA384, SHA512, SHANNON, ENTROPY, FILE INTEGRITY, FAST, MULTI-THREADED, FREE Add to Download Basket Report virus or spyware |
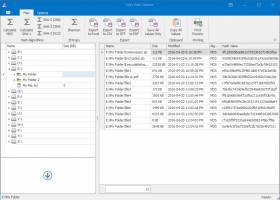 [ Zoom screenshot ] |
|
| Software Info | |
|
Best Vista Download periodically updates pricing and software information of Toms Hash Explorer full version from the publisher,
but some information may be out-of-date. You should confirm all information. Software piracy is theft, using crack, warez passwords, patches, serial numbers, registration codes, key generator, keymaker or keygen for Toms Hash Explorer license key is illegal and prevent future development of Toms Hash Explorer. Download links are directly from our mirrors or publisher's website, Toms Hash Explorer torrent files or shared files from rapidshare, yousendit or megaupload are not allowed! |
|
| Released: | August 20, 2016 |
| Filesize: | 17.44 MB |
| Language: | English |
| Platform: | Win2000, Windows XP, Windows 7 x32, Windows 7 x64, Windows 8, Windows 10, WinServer, WinOther, Windows Vista, Windows Vista x64 |
| Requirements: | Microsoft .NET Framework 4.5.2 |
| Install | Install and Uninstall |
| Add Your Review or Windows Vista Compatibility Report |
Toms Hash Explorer- Releases History |
| Software: | Toms Hash Explorer 1.2 |
| Date Released: | Aug 20, 2016 |
| Status: | Minor Update |
| Release Notes: | File Integrity Verification/Batch Verification |
| Software: | Toms Hash Explorer 1.1 |
| Date Released: | Apr 29, 2016 |
| Status: | New Release |
| Release Notes: | Themes/Skin Support, Drag and Drop, and File Entropy Computation using Shannon's Entropy Algorithm. |
Most popular single user in Encryption Tools downloads for Vista |
|
Batch File Encrypt Free 5.0.124 download by BinaryMark
... symmetric algorithms. You can encrypt files with a single password or specify cryptographic keys (vectors) instead. You ... branching. Detailed processing logs are available in both user interface and log files. Run multiple program instances ...
type: Shareware
View Details
Download
categories: batch, multiple, bulk, mass, files, encrypt, file encryption, decrypt, aes, 3-des, des, rc2, symmetric, algorithm, cryptographic, key, password, vector, bit strength |
 |
|
EaseFilter Folder Locker 5.6.1.1 download by EaseFilter Inc.
... authorize or deny the file access to specific user or process, also allow you to hide the ... filter driver and registry filter driver. In a single solution, EaseFilter Comprehensive File Security SDK encompasses file ...
type: Freeware
View Details
Download
categories: folder locker, file locker, access control, file encryption, secure file sharing, file access rights, file access, file control, file read, file write, file rename, file change, digital rights |
 |
|
Cryptosystem ME6 15.0 download by Hermetic Systems
... encryption system to encrypt information in either a single file or in multiple files (at once) so ... of files which can be encrypted in a single operation is unlimited. You can encrypt a single ...
type: Freeware
View Details
Download
categories: encryption, secure, storage, security, encipherment, cryptography, file, data |
 |
|
CryptoExpert 8 8.39 download by InterCrypto Software
... to provide secure offline storages for Windows 7 users. Physically your documents are stored in the single encrypted vault file, but in the unlocked state ... 8-th edition of the software provides completely new user interface especially designed for Windows 7 users. As ...
View Details
Download
|
 |
|
BestCrypt Traveller 1.06 download by Jetico Inc
... without installation of the software. After running a single executable file (BCTraveller.exe), a standard BestCrypt icon appears ... not require installation, registration or licensing. So, travelling users may download it from any place in the ...
type: Freeware
View Details
Download
categories: encryption software, BestCrypt encryption, access container file, BestCrypt, encryption, container |
 |
|
Toms Hash Explorer 1.2 download by Tom Andreas Mannerud
... cryptographic hash calculation suite with an innovative Explorer-like user interface. This free Windows utility allows you to easily calculate cryptographic hash values for single files or entire folders to verify file integrity. ...
type: Freeware
View Details
Download
categories: CRYPTO, HASH, HASHING, MD5, SHA, SHA-1, SHA-2, SHA256, SHA384, SHA512, SHANNON, ENTROPY, FILE INTEGRITY, FAST, MULTI-THREADED, FREE |
 |
|
IMProcessor 3.5 download by Bigboot Software
... again using a Unique password supplied by the user and finally it is encrypted again with a different key and merged with the image.The file created will look like any ...
type: Demo ($45.00)
View Details
Download
categories: Steganography, image, files, software, encrypted, encryption, Improcessor, hidden, backup |
 |
|
Speedcrypt 1.0 download by Mariano Ortu
... security features are implemented correctly. Speedcrypt provides its users with protection against Dictionary Attacks, Guessing Attacks or ... Master Key is inserted, Speedcrypt it helps the user to make the key as strong as possible, ...
View Details
Download
|
 |
|
PPT to EXE Converter Enterprise 6.21 download by VaySoft LTD.
... computer. PPT to EXE Converter Enterprise can do Single conversion and Batch conversion. PPT to EXE Converter ... can strongly protect your PPT file, Only permited user can view the presentation, with no editing, no ...
type: Shareware ($128.00)
View Details
Download
categories: powerpoint to exe, ppt to exe, powerpoint exe, ppt exe, powerpoint exe convert, ppt exe convert, embed font, powerpoint slide show, slide show, ppt to cd, powerpoint to cd, embed special fonts, powerpoint embed fonts, powerpoint embed special fonts |
 |
|
DICOM Anonymizer&Masker 1.11 download by DICOM Tool
... on. DICOM Anonymizer&Maker can: -Anonymize any Data Element: user can define a list of elements to be ... -Anonymize annotations burned in image pixels and/or overlays: user can specify different anonymization region for different images/overlays ...
type: Commercial ($38.00)
View Details
Download
categories: DICOM Anonymizer, DICOM, DICOM Anonymizer Light, DVTk, DICOManonymizer, DICOMdumper, MIRC, DICOM Randomizer, DICOM Rewriter, MIView, CTP, Santesoft, RUBY DICOM, OFFIS, Escape Medical Viewer, OsiriX, NeoLogica, Madena, DCM4CHE, DICOM Editor, Algom |
 |