Related Keywords
presence downloadsvirtual presence downloads
online presence downloads
sharepoint presence downloads
internet presence downloads
Top Software Keywords
free downloadsclean downloads
hide downloads
erase downloads
delete downloads
keylogger downloads
crack downloads
file downloads
wipe downloads
password downloads
remove downloads
cookies downloads
history downloads
security downloads
secure downloads
privacy downloads
recover downloads
protect downloads
internet downloads
cleaner downloads
shredder downloads
password recovery downloads
cache downloads
windows downloads
lost password downloads
recovery downloads
stealth downloads
utility downloads
kazaa downloads
freeraser downloads
Vista Download
Vista downloadVista antivirus download
Vista wallpaper download
Vista wallpapers download
Vista themes download
Vista pack download
Vista ultimate download
Vista home download
Vista basic download
Vista business download
Vista x64 download
Vista transformation download
Vista transformation pack download
Vista boot download
Vista dvd download
Vista sidebar download
Vista aero download
Vista product key download
Top Downloads
Top Rated
Navigation: Home
\ Security & Privacy
\ Other \ Malicious File Hunter
Malicious File Hunter2.1 by Malicious File Hunter |

|
Software Description:
... allows IT Security Administrators to search for the presence of one or multiple files across their entire network of Windows systems. For example, if a known malicious file is found on one computer, an IT Administrator can use MFH to check if any other system on the network is infected with the same malware. Search query is based on full, partial or wild card ...
type: Demo ($130.00)
Download Malicious File Huntercategories: malware finder, search malware on network, network file search, network file finder, locate malicious file, malicious file finder Add to Download Basket Report virus or spyware |
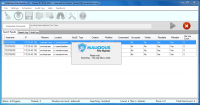 [ Zoom screenshot ] |
|
| Software Info | |
|
Best Vista Download periodically updates pricing and software information of Malicious File Hunter full version from the publisher,
but some information may be out-of-date. You should confirm all information. Software piracy is theft, using crack, warez passwords, patches, serial numbers, registration codes, key generator, keymaker or keygen for Malicious File Hunter license key is illegal and prevent future development of Malicious File Hunter. Download links are directly from our mirrors or publisher's website, Malicious File Hunter torrent files or shared files from rapidshare, yousendit or megaupload are not allowed! |
|
| Released: | January 04, 2014 |
| Filesize: | 4.00 MB |
| Language: | English |
| Platform: | Windows XP, Windows Vista, Windows Vista x64, Windows 7 x32, Windows 7 x64, Windows 2003, WinServer, Windows Vista, Windows Vista x64, Windows Vista, Windows Vista |
| Requirements: | .NET Framework 4.0, Visual C++ 2010 x86 |
| Install | Install and Uninstall |
| Add Your Review or Windows Vista Compatibility Report |
Malicious File Hunter- Releases History |
| Software: | Malicious File Hunter 2.1 |
| Date Released: | Jan 4, 2014 |
| Status: | Major Update |
| Release Notes: | - Added Copy to Share Feature - Refined search within results - Added an option to pop up Computers & Accounts if missing details - Fixed an exception when searching using IP range - Updated About screen - Fixed an issue with License Activation popup text validation |
Most popular presence in Other downloads for Vista |
|
BlackBeltPrivacy 14.2024.08.2 download by BlackBeltPrivacy Team
... choice for anyone looking to safeguard their digital presence. In summary, BlackBeltPrivacy is more than just a privacy tool; it is a comprehensive suite designed to empower users with ...
type: Open Source
View Details
Download
categories: BlackBeltPrivacy, download BlackBeltPrivacy, BlackBeltPrivacy free download, Internet privacy bundle, Internet security package, protect personal privacy, WASTE, MicroSIP, Tor, bundle |
 |
|
Detekt 2.0 download by Botherder
... utility is equipped to recognize and signal the presence of a variety of spyware tools,including DarkComet RAT, BlackShades RAT, HackingTeam RCS, FinFisher FinSpy, njRAT and others. Should any of these ...
type: Freeware
View Details
Download
categories: spyware detector, spyware scanner, detect spyware, detector, detect, scanner, scan |
 |
|
Terminator 8.1 download by GKC ElectroSoft
... around-the-clock protection of your information, even without your presence. 6. Terminator System saves your money One Terminator System, installed on any computer within the network, controls the information on all ...
type: Shareware ($19.00)
View Details
Download
categories: data deleter, remote data deleter, remote computer control, remote, deleter, delete |
 |
|
FastAccess Pro 5.0.90 SR download by Sensible Vision
... login. Only FastAccess can continuously track for the presence of your face after login in order to automatically secure your desktop and/or web passwords when you walk away. Gain ...
type: Trialware ($24.99)
View Details
Download
categories: face recognition, facial recognition, computer security, face, facial, recognition |
 |
|
Hidden Cmd Detector 1.5 download by SecurityXploded
... discover Hidden Command prompts and detect any Hacker presence on your system. The first thing any Hacker does on getting access to remote system is to run a hidden Command ...
type: Freeware
View Details
Download
categories: cmd.exe finder, hacker detector, command prompt finder, find command shell, hidden cmd prompt, cmd shell tool |
 |
|
Remo Privacy Cleaner 1.0.0.35 download by Remo Software
... one of the reasons could be the excess presence of junk files in your browser. Remo Privacy Cleaner app will help you say goodbye to all that by running a ...
type: Demo ($29.97)
View Details
Download
categories: privacy cleaner, privacy cleaner app, clean cache and cookies, clean junk data, delete browser history, privacy app, delete junk files, clean registry, clean junk apps, clean free space |
 |
|
Malicious File Hunter 2.1 download by Malicious File Hunter
... allows IT Security Administrators to search for the presence of one or multiple files across their entire network of Windows systems. For example, if a known malicious file is found ...
type: Demo ($130.00)
View Details
Download
categories: malware finder, search malware on network, network file search, network file finder, locate malicious file, malicious file finder |
|
DLL Magic 1.0 download by SecurityXploded
... common method used by Rootkits to hide their presence. However such hidden DLLs are visible in Kernel based tools. Though 'DLL Magic' works on both 32-bit & 64-bit systems, it ...
type: Freeware
View Details
Download
categories: hide dll, hide dll tool, dll hiding tool, hide module, hide injected dll, dll magic |
 |