Related Keywords
point downloadspoint q downloads
point to point tunneling downloads
point to point communication downloads
point of sale downloads
point of sale software downloads
point of sale system downloads
point of purchase downloads
point of sale retail software downloads
point sale inventory software downloads
point of sales downloads
point sale software downloads
point retail sale software downloads
point restaurant sale software downloads
point charts downloads
point list downloads
point import downloads
point speak downloads
point hunter downloads
point and click interface downloads
Top Software Keywords
decrypt downloadsencryption downloads
aes downloads
safe downloads
encryption software downloads
folder lock downloads
decryption downloads
file encryption downloads
privacy downloads
secure downloads
data encryption downloads
password downloads
recovery downloads
security downloads
encrypt downloads
files downloads
file downloads
protection downloads
email downloads
folder downloads
protect downloads
crack downloads
hide downloads
blowfish downloads
folders downloads
lock downloads
lock folder downloads
recover downloads
rijndael downloads
des downloads
Vista Download
Vista downloadVista antivirus download
Vista wallpaper download
Vista wallpapers download
Vista themes download
Vista pack download
Vista ultimate download
Vista home download
Vista basic download
Vista business download
Vista x64 download
Vista transformation download
Vista transformation pack download
Vista boot download
Vista dvd download
Vista sidebar download
Vista aero download
Vista product key download
Top Downloads
Top Rated
Navigation: Home
\ Security & Privacy
\ Encryption Tools \ ProxyCrypt
ProxyCrypt2.6.3 by v77 |

|
Software Description:
ProxyCrypt is a command line tool that creates encrypted volumes within a file or a hard drive. Designed for paranoids and advanced users, it is also fast, very lightweight, open source and easy to recompile. It works as a 'proxy' for the ImDisk driver, which is included in the full package. If you need to create encrypted spaces which can be partitioned like an ordinary hard drive, it is also compatible with Arsenal Image Mounter. ...
Download ProxyCryptAdd to Download Basket Report virus or spyware |
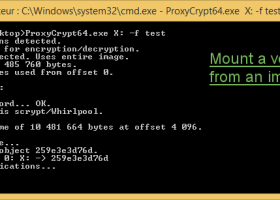 [ Zoom screenshot ] |
|
| Software Info | |
|
Best Vista Download periodically updates pricing and software information of ProxyCrypt full version from the publisher,
but some information may be out-of-date. You should confirm all information. Software piracy is theft, using crack, warez passwords, patches, serial numbers, registration codes, key generator, keymaker or keygen for ProxyCrypt license key is illegal and prevent future development of ProxyCrypt. Download links are directly from our mirrors or publisher's website, ProxyCrypt torrent files or shared files from rapidshare, yousendit or megaupload are not allowed! |
|
| Released: | March 06, 2022 |
| Filesize: | 467 kB |
| Language: | English |
| Platform: | Win2000, Windows XP, Windows 7 x32, Windows 7 x64, Windows 8, Windows 10, WinServer, WinOther, Windows Vista, Windows Vista x64 |
| Requirements: | - ImDisk or Arsenal Image Mounter - Administrative privileges - CPU with SSE2 |
| Install | No Install Support |
| Add Your Review or Windows Vista Compatibility Report |
ProxyCrypt- Releases History |
| Software: | ProxyCrypt 2.6.3 |
| Date Released: | Mar 6, 2022 |
| Status: | Minor Update |
| Release Notes: | - updated driver to version 2.1.1 in full package - updated MinGW from 10.2.1 to 11.2.1 |
| Software: | ProxyCrypt 2.6.2 |
| Date Released: | Apr 29, 2021 |
| Status: | Minor Update |
| Release Notes: | - added a sound ("bell" character) in case of password or hash file error |
| Software: | ProxyCrypt 2.6.0 |
| Date Released: | Oct 21, 2020 |
| Status: | New Release |
| Release Notes: | - added an option to change the font and colors of the current console (Vista and later) - critical error messages are now displayed in message boxes, with option to retry when possible - updated MinGW from 7.3.0 to 10.2.1 (released by LH_Mouse) - improved optimization script - minor fixes |
Most popular point q in Encryption Tools downloads for Vista |
|
DeCypherIT 2.0.6 download by Cypherix
... IT. It is very easy to use. Simply point to the location of the encrypted file and enter the password. That's it !. Click here to download DeCypherIT, a free ...
type: Freeware
View Details
Download
categories: decrypt archive, open encrypted archive, SIT archive opener, decrypt, unprotect, open |
 |
|
ProxyCrypt 2.6.3 download by v77
... - NTFS folders can be used as mount point instead of drive letters. - Supports very long paths of image file (more than 260 characters). - Performances improved with AES ...
View Details
Download
|
 |
|
IMProcessor 3.5 download by Bigboot Software
... in seemingly harmless files to protect information. The point of steganography is the fact that nobody will ever try to look for the secret file that was created, because they ...
type: Demo ($45.00)
View Details
Download
categories: Steganography, image, files, software, encrypted, encryption, Improcessor, hidden, backup |
 |
|
abylon BASIC 23.60.1 download by abylonsoft - Dr. Thomas Klabunde
... click under the entry 'abylon CRYPT' on the point 'Encrypt' and enter a password or insert a smartcard into your card reader. Supported cards are the 'EC MoneyCard' with chip, ...
type: Shareware ($25.50)
View Details
Download
categories: sign, crypt, code, signing, coding, encryption, security, PKCS, plugin, utilitie, SME, digital envelop, encode, compress, zip, attachment, explorer, email, mapi, manager, cookies, history, WinCrypt, apm, abylon protection manager |
 |
|
Digital Document Encryptor 2011 download by SafeIT Security
... and a browser to decrypt the e-mail locally. Point-to-point e-mail security ®. Select files or folders through the easy to use interface or simply right click on a file or ...
type: Commercial ($39.95)
View Details
Download
categories: Encrypt, Secure, Attachment, Safe, Encryption, Password, Lock, Security |
 |
|
BestCrypt Volume Encryption 5.12.3 download by Jetico Inc
... volume consisting of one disk partition. * Mount point - volume mounted as a sub-folder on NTFS-formatted volume. * Multipartition volume, i.e. volume consisting of several disk partitions: 1. Spanned ...
type: Trialware ($99.95)
View Details
Download
categories: Volume Encryption, encryption algorithm, encryption key, Encryption, Encrypt, Encrypter |
 |
|
PDF No Copy for Desktop 1.0 download by pdf-no-copy.com
... plagiarists to use your text. This is the point to mention that not all PDF readers respect these restrictions. In order to fully prevent others from copying the content of ...
type: Freeware
View Details
Download
categories: PDF, copy, paste, protection, protections, DRM, disable, protected, no copy, free, easy, simple, fast, protect |
 |
|
GhostVolt 1.3.3.0 download by GhostVolt
... data security and an uninterrupted work-flow at every point on your network. Automated encryption not only saves time and cost but also eliminates the threat of human error and helps ...
type: Demo ($40.00)
View Details
Download
categories: encryption, security, privacy, Data protection, Data privacy, File encryption, Folder encryption, Data control, HIPPA |
 |
|
GhostVolt Business Edition 1.3.3.0 download by GhostVolt
... data security and an uninterrupted work-flow at every point on your network. Automated encryption not only saves time and cost but also eliminates the threat of human error and helps ...
type: Demo ($85.00)
View Details
Download
categories: anti-ransomware, encryption, security, privacy, collaboration, Data privacy, File encryption, file-sharing, Data control, HIPPA |
 |
|
Cryptainer Enterprise Encryption Software 17.0.2.0 download by Cypherix Software
... even with the password. Administrative module provides single point control and monitoring of distributed vaults. Cryptainer Enterprise protects any file, folder, pictures, media with strong encryption on any Windows PC. ...
type: Shareware ($139.95)
View Details
Download
categories: enterprise encryption software, encryption software, best encryption software, business encryption software, corporate encryption software, data encryption, folder encryption, file encryption, disk encryption, email encryption, encryption |
 |