Related Keywords
on the time downloadstime on the desktop downloads
the file encryption on the go downloads
on the fly encryption downloads
on the fly downloads
on the flight encryption downloads
on the fiy encryption downloads
on the fly encrypting downloads
on the range user selected downloads
on the earth downloads
on the fly as an audio disc downloads
on the very top of downloads
on the left of your screen downloads
on the fly backup downloads
on the screen downloads
on the beach downloads
on the way theme downloads
on the same downloads
on the fly disk encryption downloads
on the moon downloads
Top Software Keywords
decrypt downloadsencryption downloads
aes downloads
safe downloads
encryption software downloads
file encryption downloads
decryption downloads
privacy downloads
data encryption downloads
folder lock downloads
secure downloads
password downloads
security downloads
recovery downloads
files downloads
encrypt downloads
protection downloads
file downloads
email downloads
folder downloads
protect downloads
crack downloads
hide downloads
blowfish downloads
folders downloads
lock downloads
lock folder downloads
recover downloads
rijndael downloads
des downloads
Vista Download
Vista downloadVista antivirus download
Vista wallpaper download
Vista wallpapers download
Vista themes download
Vista pack download
Vista ultimate download
Vista home download
Vista basic download
Vista business download
Vista x64 download
Vista transformation download
Vista transformation pack download
Vista boot download
Vista dvd download
Vista sidebar download
Vista aero download
Vista product key download
Top Downloads
Top Rated
Navigation: Home
\ Security & Privacy
\ Encryption Tools \ abylon CRYPT in the BOX
abylon CRYPT in the BOX2014 by Logosec.de |

|
Software Description:
The file-safe automatically encrypts all files in the CRYPT-folder without entering the password every time. The the one-time entry of the password is sufficient to access the saved files and unauthorized users can not open this. Changes in the files will be updateded in the encrypted files automatically and the file-based design enables simultaneous access to multiple authorized ...
type: Shareware
Download abylon CRYPT in the BOXcategories: Strong, Encryption, security, access, AES, password, directory, Automatic, Simple, Easy, folders, drag and drop, locked up, cryptography, multi-user, background, auto encryption, file, data, files Buy Now Add to Download Basket Report virus or spyware |
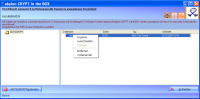 [ Zoom screenshot ] |
|
| Software Info | |
|
Best Vista Download periodically updates pricing and software information of abylon CRYPT in the BOX full version from the publisher,
but some information may be out-of-date. You should confirm all information. Software piracy is theft, using crack, warez passwords, patches, serial numbers, registration codes, key generator, keymaker or keygen for abylon CRYPT in the BOX license key is illegal and prevent future development of abylon CRYPT in the BOX. Download links are directly from our mirrors or publisher's website, abylon CRYPT in the BOX torrent files or shared files from rapidshare, yousendit or megaupload are not allowed! |
|
| Website: | Logosec.de - abylon CRYPT in the BOX homepage |
| Released: | November 01, 2013 |
| Filesize: | 15.83 MB |
| Language: | German, English, Spanish, French |
| Platform: | Win2000, Windows 7 x32, Windows 7 x64, Windows 8, Windows 8.1, WinServer, Windows Vista, Windows Vista x64, Windows XP |
| Requirements: | Pentium; 256MB RAM |
| Install | Install and Uninstall |
| Add Your Review or Windows Vista Compatibility Report |
abylon CRYPT in the BOX- Releases History |
| Software: | abylon CRYPT in the BOX 2014 |
| Date Released: | Nov 1, 2013 |
| Status: | Major Update |
| Release Notes: | Neue Funktionen und Verbesserungen, Winbdows 8 und 8.1 Support |
| Software: | abylon CRYPT in the BOX 2011.7 |
| Date Released: | Jan 20, 2012 |
| Status: | New Release |
| Release Notes: | Neue Oberfläche, 64bit Support |
Most popular on the time in Encryption Tools downloads for Vista |
|
Hash Codes 1.62.780.7200 download by Marek Sienczak
... TIGER and Whirlpool algorithm Copy hash codes to the clipboard or save to the disk Can compare hash codes Load saved hash code file to comparison The progress bar show the current process Suspend, resume ...
View Details
Download
|
 |
|
DICOM Anonymizer&Masker 1.11 download by DICOM Tool
... many cases, prior to publishing (for instance, on the Web) or distributing in any way DICOM files ... patient's or physicians' privacy. This information, embedded into the DICOM file along with the actual image(s) or ...
type: Commercial ($38.00)
View Details
Download
categories: DICOM Anonymizer, DICOM, DICOM Anonymizer Light, DVTk, DICOManonymizer, DICOMdumper, MIRC, DICOM Randomizer, DICOM Rewriter, MIView, CTP, Santesoft, RUBY DICOM, OFFIS, Escape Medical Viewer, OsiriX, NeoLogica, Madena, DCM4CHE, DICOM Editor, Algom |
 |
|
DirCryptHide 1.58 download by Gunnar Daehling
... file will mount as another drive. When moving the data is first copied, while no error occurs, the original folder is deleted, at the direction of the container, the data can be ...
type: Freeware
View Details
Download
categories: Encryption, truecrypt, on the fly, hide folder, safe, tresor, container, hide, ordner, password, invisible, protect |
|
Hash Codes x64 1.62.780.7200 download by Marek Sienczak
... TIGER and Whirlpool algorithm Copy hash codes to the clipboard or save to the disk Can compare hash codes Load saved hash code file to comparison The progress bar show the current process Suspend, resume ...
type: Open Source
View Details
Download
categories: x64 hash data, x64 encrypt data, x64 data encryption, x64 hash, x64 encrypt, x64 encryption |
 |
|
gpg4usb 0.3.3-2 download by gpg4usb Development Team
... even one with a Microsoft-OS running. Almost the only thing required is an available usb-port you ... somewhere else on holiday... and you always have the encryption-keys available for usage! The usage of ...
View Details
Download
|
 |
|
Passper for RAR 4.0.1 download by iMyFone Technology Co.
... Brute-Force Attack. These options provide flexibility depending on the complexity and nature of the password, ensuring a higher probability of successful recovery. ... multi-core CPU acceleration, Passper for RAR significantly reduces the time required to crack passwords. This efficiency is ...
type: Demo
View Details
Download
categories: Passper for RAR, download Passper for RAR, Passper for RAR free download, RAR Password, Recover Password, Decrypt Passcode, RAR, password, archive, recover |
 |
|
Passper for PDF 4.0.0 download by iMyFone Technology Co.
... their content without compromising security. One of the standout features of Passper for PDF is its ability to recover forgotten passwords with remarkable efficiency. The software employs advanced algorithms to perform four distinct ...
type: Demo ($19.99)
View Details
Download
categories: Remove Restrictions, Passper for PDF, PDF password recovery, Recover Password, PDF, decrypt PDF files, Recover, Recovery, iMyFone Technology, unlock PDF, download Passper for PDF, Password, PDF Password, remove PDF restrictions, Passper for PDF free downl |
 |
|
Easy File Protector 5.134 download by IM-Soft
... access to your files and folders by user-defined time schedule. You choose users, define restricted files/folders and time periods for them, and activate the program. After that, your system disables/enables your files ...
type: Shareware ($39.00)
View Details
Download
categories: password, security, access, control, protect, privacy, restrict, restrictions, restricting, computer, download, free, screen, lock |
 |
|
CryptoExpert 8 8.39 download by InterCrypto Software
... 7 users. Physically your documents are stored in the single encrypted vault file, but in the unlocked state the vault is visible to all windows applications like any usual local drive. New 8-th edition of the software provides completely new user interface especially designed ...
View Details
Download
|
 |
|
XorIt 1.9 download by Sinner Computing
Most file encryptors use methods that rely on the theory of computational security, that is difficulty of key factorisation prevents decryption of the file. But this method may not work forever. ...
View Details
Download
|
 |