Related Keywords
method downloadsmethod headings downloads
method of socrates downloads
method overload downloads
numerical searching method downloads
secant method downloads
ear training method downloads
native method downloads
small s method downloads
ten finger method downloads
breathing method downloads
gutmann method downloads
mystery method downloads
fertility awareness method downloads
cyclomancy divination method downloads
sedona method downloads
pimsleur method downloads
encapsulation method downloads
japanese method downloads
statistical method downloads
Top Software Keywords
free downloadsclean downloads
hide downloads
erase downloads
delete downloads
file downloads
keylogger downloads
crack downloads
wipe downloads
password downloads
remove downloads
security downloads
history downloads
cookies downloads
secure downloads
privacy downloads
protect downloads
internet downloads
recover downloads
cleaner downloads
shredder downloads
windows downloads
cache downloads
password recovery downloads
recovery downloads
lost password downloads
stealth downloads
utility downloads
kazaa downloads
freeraser downloads
Vista Download
Vista downloadVista antivirus download
Vista wallpaper download
Vista wallpapers download
Vista themes download
Vista pack download
Vista ultimate download
Vista home download
Vista basic download
Vista business download
Vista x64 download
Vista transformation download
Vista transformation pack download
Vista boot download
Vista dvd download
Vista sidebar download
Vista aero download
Vista product key download
Top Downloads
Top Rated
Navigation: Home
\ Security & Privacy
\ Other \ Shadow Defender
Shadow Defender1.5.0.726 by Shadowdefender.com |

|
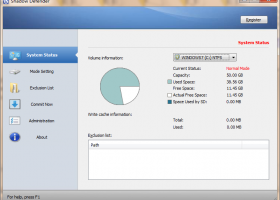
Software Description:
... and contents. Shadow Defender provides you with two methods of going into 'Shadow Mode', namely 'Exit Shadow Mode at Shutdown' and 'Enter Shadow Mode on Boot', enabling you to select whichever you prefer best. ...
type: Trialware ($39.00)
Download Shadow Defendercategories: protect privacy, cookies, data protection, protect, pc defender, protection, privacy Buy Now Add to Download Basket Report virus or spyware |
 [ Zoom screenshot ] |
|
| Software Info | |
|
Best Vista Download periodically updates pricing and software information of Shadow Defender full version from the publisher,
but some information may be out-of-date. You should confirm all information. Software piracy is theft, using crack, warez passwords, patches, serial numbers, registration codes, key generator, keymaker or keygen for Shadow Defender license key is illegal and prevent future development of Shadow Defender. Download links are directly from our mirrors or publisher's website, Shadow Defender torrent files or shared files from rapidshare, yousendit or megaupload are not allowed! |
|
| Website: | Shadowdefender.com - Shadow Defender homepage |
| Released: | August 02, 2020 |
| Filesize: | 3.50 MB |
| Platform: | Windows XP, Windows Vista, Windows Vista x64, Windows 7, Windows 7 x64, Windows 8, Windows 8 x64, Windows 10, Windows 10 x64 |
| Install | Instal And Uninstall |
| Add Your Review or Windows Vista Compatibility Report |
Shadow Defender- Releases History |
| Software: | Shadow Defender 1.5.0.726 |
| Date Released: | Aug 2, 2020 |
| Status: | New Release |
| Release Notes: | Fixed: Fix a bug related to Exclusion List on Windows 10. |
| Software: | Shadow Defender 1.4.0.680 |
| Date Released: | May 8, 2018 |
| Status: | New Release |
| Release Notes: | Fixed: An error message 'You Need to Format the Disk before You Can Use It' when enter/exit Shadow Mode. New: Some GUI changes. |
| Software: | Shadow Defender 1.4.0.672 |
| Date Released: | Nov 13, 2017 |
| Status: | New Release |
| Release Notes: | New: Supports Windows 10 Creators Update. New: Setup.exe supports command argument: /silent /config:<path-to-config-file>. New: Some GUI changes. New: Supports customized desktop tip icon. |
Most popular method in Other downloads for Vista |
|
Secure Eraser Standard Edition 6.109 download by ASCOMP Software
... recognized standards such as the DoD 5220.22-M, Gutmann method, and others. This ensures that once data is ... delete sensitive data. Its combination of advanced erasure methods, additional system optimization tools, and comprehensive reporting makes ...
type: Shareware
View Details
Download
categories: Secure Eraser, download Secure Eraser, Secure Eraser free download, secure deletion, clean registry, erase partition, eraser, shredder, cleaner, optimizer |
 |
|
SHA256 Hash Generator 1.5 download by SecurityXploded
... text. SHA256 checksum/hash is the popular and secure method of verifying files downloaded from Internet. This tool helps you to easily and instantly generate SHA256 hash for downloaded file and ...
type: Freeware
View Details
Download
categories: SHA256 hash generator, SHA256 hash calculator, SHA256 checksum calculator, SHA256 checksum generator, SHA256 hash maker, SHA256 hash tool, SHA256 checksum tool |
 |
|
Secure Eraser Standard Edition 6.109 download by ASCOMP Software
... recognized standards such as the DoD 5220.22-M, Gutmann method, and others. This ensures that once data is ... delete sensitive data. Its combination of advanced erasure methods, additional system optimization tools, and comprehensive reporting makes ...
type: Shareware
View Details
Download
categories: Secure Eraser, download Secure Eraser, Secure Eraser free download, secure deletion, clean registry, erase partition, eraser, shredder, cleaner, optimizer |
 |
|
abylon LOGON 25.10.11.1 download by abylonsoft - Dr. Thomas Klabunde GbR
... chips, this software provides a secure and efficient method for accessing your computer, eliminating the need for ... allowing users to quickly configure their preferred authentication method. 3. **Versatile Authentication Options**: Abylon LOGON supports ...
type: Trialware
View Details
Download
categories: abylon LOGON free download, security software, Dr. Thomas Klabunde, authentication, protect PC, abylon LOGON, smartcard protection, abylonsoft, protection, login, password management, download abylon LOGON, smartcard, USB-Token protection, USB-Token |
 |
|
XL Delete 2.9.2 download by -XL- Development
... will actually be overwritten several times using specialized methods to prevent data recovery software from being able ... that you want to delete. 12 Different wipe methods to choose from including Peter Gutmann's method. Define ...
View Details
Download
|
 |
|
Shadow Defender 1.5.0.726 download by Shadowdefender.com
... their initial state. Shadow Defender offers a manual method of permanently saving a file or change to ... Shadow Mode. Shadow Defender provides you with two methods of going into 'Shadow Mode', namely 'Exit Shadow ...
type: Trialware ($39.00)
View Details
Download
categories: protect privacy, cookies, data protection, protect, pc defender, protection, privacy |
 |
|
Shadow Defender x64 1.5.0.726 download by Shadowdefender.com
... Shadow Defender x64 is using a unique method called Shadow Mode to ensure PCs are protected.By placing PCs in Shadow Mode with Shadow Defender, you can be confident the ...
type: Trialware ($39.00)
View Details
Download
categories: x64 pc defender, x64 protect, x64 protection, x64 privacy, x64 protect privacy, x64 data protection, privacy |
 |
|
Net Nanny 6.5 download by ContentWatch
... secure proxies (example: UltraSurf) is the number one method used by tech-savvy teens to circumvent desktop filters. This includes proxies, secure proxies, and local host proxies or application proxies. ...
type: Trialware ($39.99)
View Details
Download
categories: filter, security, privacy, control, monitoring, child, kids, netnanny |
 |
|
Rohos Face Logon 5.2 download by Tesline-Service.SRL
... designed to add authentication convenience and additional security method to the standard Windows logon procedure. It allows to access Windows computer in an easy, fast and secure way by using ...
type: Trialware ($13.56)
View Details
Download
categories: login authentication, face recognition, Windows login, authentication, login, face |
 |
|
File Shredder 4.1.2 download by Kakasoft
... it several times with US Dod 5220.22-M erasure method. With File Shredder you can securely delete files and documents from your hard drive without fearing that they could be ...
View Details
Download
|
 |