Related Keywords
image downloadsimage f downloads
image into nude image downloads
image cut (image splitter) downloads
image within an image downloads
image cut image splitter downloads
image resize photos change size image resizer downloads
image map downloads
image frames downloads
image tools downloads
image converter downloads
image conversion downloads
image edit downloads
image capture downloads
image gallery downloads
image viewer downloads
image editor downloads
image editing downloads
image format downloads
image encryption downloads
Top Software Keywords
decrypt downloadsencryption downloads
aes downloads
safe downloads
encryption software downloads
file encryption downloads
decryption downloads
privacy downloads
data encryption downloads
secure downloads
folder lock downloads
password downloads
security downloads
files downloads
recovery downloads
encrypt downloads
protection downloads
file downloads
email downloads
folder downloads
protect downloads
crack downloads
hide downloads
blowfish downloads
folders downloads
lock downloads
lock folder downloads
recover downloads
rijndael downloads
des downloads
Vista Download
Vista downloadVista antivirus download
Vista wallpaper download
Vista wallpapers download
Vista themes download
Vista pack download
Vista ultimate download
Vista home download
Vista basic download
Vista business download
Vista x64 download
Vista transformation download
Vista transformation pack download
Vista boot download
Vista dvd download
Vista sidebar download
Vista aero download
Vista product key download
Top Downloads
Top Rated
Navigation: Home
\ Security & Privacy
\ Encryption Tools \ ProxyCrypt
ProxyCrypt2.6.3 by v77 |

|
Software Description:
... hard drive, it is also compatible with Arsenal Image Mounter. ...
Download ProxyCryptAdd to Download Basket Report virus or spyware |
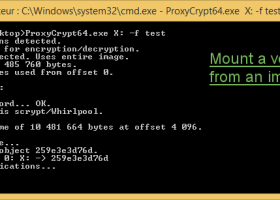 [ Zoom screenshot ] |
|
| Software Info | |
|
Best Vista Download periodically updates pricing and software information of ProxyCrypt full version from the publisher,
but some information may be out-of-date. You should confirm all information. Software piracy is theft, using crack, warez passwords, patches, serial numbers, registration codes, key generator, keymaker or keygen for ProxyCrypt license key is illegal and prevent future development of ProxyCrypt. Download links are directly from our mirrors or publisher's website, ProxyCrypt torrent files or shared files from rapidshare, yousendit or megaupload are not allowed! |
|
| Released: | March 06, 2022 |
| Filesize: | 467 kB |
| Language: | English |
| Platform: | Win2000, Windows XP, Windows 7 x32, Windows 7 x64, Windows 8, Windows 10, WinServer, WinOther, Windows Vista, Windows Vista x64 |
| Requirements: | - ImDisk or Arsenal Image Mounter - Administrative privileges - CPU with SSE2 |
| Install | No Install Support |
| Add Your Review or Windows Vista Compatibility Report |
ProxyCrypt- Releases History |
| Software: | ProxyCrypt 2.6.3 |
| Date Released: | Mar 6, 2022 |
| Status: | Minor Update |
| Release Notes: | - updated driver to version 2.1.1 in full package - updated MinGW from 10.2.1 to 11.2.1 |
| Software: | ProxyCrypt 2.6.2 |
| Date Released: | Apr 29, 2021 |
| Status: | Minor Update |
| Release Notes: | - added a sound ("bell" character) in case of password or hash file error |
| Software: | ProxyCrypt 2.6.0 |
| Date Released: | Oct 21, 2020 |
| Status: | New Release |
| Release Notes: | - added an option to change the font and colors of the current console (Vista and later) - critical error messages are now displayed in message boxes, with option to retry when possible - updated MinGW from 7.3.0 to 10.2.1 (released by LH_Mouse) - improved optimization script - minor fixes |
Most popular image in Encryption Tools downloads for Vista |
|
Simple Image Steganography 1.2.4a download by Robert Abraham
"Simple Image Steganography" is an intriguing software solution developed by ... effective approach to embedding hidden messages within digital images, making it a valuable tool for those who ... in their communications. At its core, Simple Image Steganography leverages the least significant bit (LSB) technique, ...
type: Open Source
View Details
Download
categories: Simple Image Steganography, download Simple Image Steganography, Simple Image Steganography free download, image steganography, hide file, steganography app, steganography, hide, conceal, carrier |
 |
|
Paranoia Text Encryption for PC 15.0.4 download by Paranoia Works
... implementation is included (concealing a text within an image - JPG). A steganographic algorithm (F5 algorithm) is ... cipher algorithm to make a final steganogram (JPEG image). Fully compatible with Paranoia Text Encryption for iOS ...
type: Freeware
View Details
Download
categories: encryption, encrypter, encryptor, encrypt, note, notes, text, texts, messages, chat, email, emails, sms, social, ciphering, encipher, aes, blowfish, threefish, serpent, 256, 512, 1024, bit, bits, steganography, JPG, cryptocurrency, seed, mnemonic, key, keys, safe, vault, password |
 |
|
ProxyCrypt 2.6.3 download by v77
... hard drive, ProxyCrypt is also compatible with Arsenal Image Mounter. Features: - Supports AES-256, Serpent and SHACAL-2 ... 250 characters. - Protection against keyloggers. - Supports image files or physical drives with MBR (with extended ...
View Details
Download
|
 |
|
DiskEncryptor 1.8 download by KernSafe Technology
... virtual disk and cdrom emluator. Encrypt the CD/DVD images and save your private data in .iso files ... Card and floppy disk. Support for encrypt cd/dvd image(.iso) for mount to virtual cdrom or burn to ...
type: Freeware
View Details
Download
categories: encryption, disk encryption, cd encrypt, cd password, cd protect, disk encrypt, virtual disk, emulator |
 |
|
VaySoft Video to EXE Converter 6.27 download by VaySoft LTD.
... file. For example you can set private icon images for output exe file and configure your picture images before or after playing the video. The image support not only JPG, BMP,EMF but also PNG ...
type: Shareware ($45.00)
View Details
Download
categories: video to exe, protect video file, avi to exe, asf to exe, wmv to exe |
 |
|
Secure Disc Creator 8.5.11 download by GiliSoft International LLC.
... a high degree of protection. 6. Make ISO Image File: Users can create ISO images of their discs, facilitating easy storage and duplication of data. 7. Burning ISO Image File: The software can burn ISO image files ...
View Details
Download
|
 |
|
DICOM Anonymizer&Masker 1.11 download by DICOM Tool
... distributing in any way DICOM files containing medical images of interest, it is necessary to remove all ... into the DICOM file along with the actual image(s) or even burned in the actual image(s) and ...
type: Commercial ($38.00)
View Details
Download
categories: DICOM Anonymizer, DICOM, DICOM Anonymizer Light, DVTk, DICOManonymizer, DICOMdumper, MIRC, DICOM Randomizer, DICOM Rewriter, MIView, CTP, Santesoft, RUBY DICOM, OFFIS, Escape Medical Viewer, OsiriX, NeoLogica, Madena, DCM4CHE, DICOM Editor, Algom |
 |
|
Free File Camouflage 1.25 download by My Portable Software
... hide and protect your files inside a jpeg image! The software can be used with the main ... only need to select a directory with some images). All the files are encrypted using AES and ...
type: Commercial
View Details
Download
categories: camouflage file, hide document, decrypt file, camouflage, hide, disguise, decrypt |
 |
|
IMProcessor 3.5 download by Bigboot Software
... problem because it hides your sensitive information within image files such as holiday picture. The hidden files ... type and the number of files hidden per image is not limited. The hidden files have multiple ...
type: Demo ($45.00)
View Details
Download
categories: Steganography, image, files, software, encrypted, encryption, Improcessor, hidden, backup |
 |
|
Confidential Free Edition 1.0 download by Eagle-Soft
... the world. It allows you to hide an image and/or text within a visible image. Confidential uses the AES-256 bits encryption algorithm as ... control of totalitarian regimes. Concealing sensitive documents. The image containing the hidden data is compatible with: The ...
View Details
Download
|
 |