Related Keywords
file date time downloadschange file date time downloads
date time stamp downloads
date time downloads
date time change downloads
date time picker downloads
date time stamp software downloads
date time stamper downloads
date time charts downloads
date time chart downloads
file date downloads
file date change downloads
file date changer downloads
file date finder downloads
file date tool downloads
add date time downloads
dv video date time stamp downloads
jpg jpeg photo date time stamp downloads
add the date time to photo downloads
saving with date time downloads
Top Software Keywords
free downloadsclean downloads
hide downloads
erase downloads
delete downloads
file downloads
keylogger downloads
crack downloads
wipe downloads
password downloads
remove downloads
security downloads
history downloads
cookies downloads
secure downloads
privacy downloads
protect downloads
internet downloads
recover downloads
cleaner downloads
shredder downloads
windows downloads
cache downloads
password recovery downloads
recovery downloads
lost password downloads
stealth downloads
utility downloads
kazaa downloads
freeraser downloads
Vista Download
Vista downloadVista antivirus download
Vista wallpaper download
Vista wallpapers download
Vista themes download
Vista pack download
Vista ultimate download
Vista home download
Vista basic download
Vista business download
Vista x64 download
Vista transformation download
Vista transformation pack download
Vista boot download
Vista dvd download
Vista sidebar download
Vista aero download
Vista product key download
Top Downloads
Top Rated
Navigation: Home
\ Security & Privacy
\ Other \ Data Destroyer
Data Destroyer17.07 by Hermetic Systems |

|
Software Description:
A program for secure file deletion which overwrites data in specified files so that the data cannot be recovered by any means. A single file can be purged or, in batch mode, multiple files. Selected subfolders of a folder can be purged. ... speed can be tested for an estimation of time required. Can wipe files older than a specified date. Can wipe files in the Windows 7 and 8 Recycle Bin. ...
type: Shareware ($27.95)
Download Data Destroyercategories: data destroyer, disk, purge, file purge, secure deletion, secure file deletion, sanitize, sanitization, DoD, Defense, 5220.22-M, file deletion Buy Now Add to Download Basket Report virus or spyware |
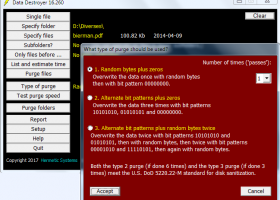 [ Zoom screenshot ] |

|
|
| Software Info | |
|
Best Vista Download periodically updates pricing and software information of Data Destroyer full version from the publisher,
but some information may be out-of-date. You should confirm all information. Software piracy is theft, using crack, warez passwords, patches, serial numbers, registration codes, key generator, keymaker or keygen for Data Destroyer license key is illegal and prevent future development of Data Destroyer. Download links are directly from our mirrors or publisher's website, Data Destroyer torrent files or shared files from rapidshare, yousendit or megaupload are not allowed! |
|
| Website: | Hermetic Systems - Data Destroyer homepage |
| Released: | March 02, 2018 |
| Filesize: | 1.69 MB |
| Language: | English |
| Platform: | Win XP, Win 98, Win 2000, Windows Vista x32, Windows Vista x64, Windows 7 x32, Windows 7 x64, Win8 x32, Win8 x64, Win10 x32, Win10 x64 |
| Install | Install and Uninstall |
| Add Your Review or Windows Vista Compatibility Report |
Data Destroyer- Releases History |
| Software: | Data Destroyer 17.07 |
| Date Released: | Oct 30, 2017 |
| Status: | Minor Update |
| Release Notes: | Improved trial version |
| Software: | Data Destroyer 17.06 |
| Date Released: | Aug 10, 2017 |
| Status: | Major Update |
| Release Notes: | Improved startup of activated version |
| Software: | Data Destroyer 16.26 |
| Date Released: | Jul 2, 2017 |
| Status: | Minor Update |
| Release Notes: | Windows 10 compatible installer |
Most popular file date time in Other downloads for Vista |
|
Ardamax Keylogger 4.8 download by Ardamax Software
... it and save it to a hidden log file for you to view at a later date. Email log delivery - Ardamax Keylogger can send your recorded logs via e-mail at set times - perfect for remote monitoring! Application tracking - ...
View Details
Download
|
 |
|
Action1 Network Discovery Free Edition 2.6 download by Action1 Corporation
... or IIS running? - List of endpoints exposing file shares to ransomware. - Show endpoints with remote ... any of your endpoints. - Users storing sensitive files locally on unsecured laptops. - Systems at risk ...
type: Freeware
View Details
Download
categories: network mapping, network discovery, free network discovery tool, free network mapping tool |
 |
|
Action1 Software Inventory Manager 2.6 download by Action1 Corporation
... or IIS running? - List of endpoints exposing file shares to ransomware. - Show endpoints with remote ... any of your endpoints. - Users storing sensitive files locally on unsecured laptops. - Systems at risk ...
type: Freeware
View Details
Download
categories: free software inventory management, installed software, software audit scanning, network software scanner, IT asset management |
 |
|
Best Free Keylogger 7.2.0 download by bestxsoftware
... can monitor specific users, specific applications during specific time periods. You can also configure Best Free Keylogger to uninstall automatically on a specific date without being detected to the user. Parental controls ...
type: Freeware
View Details
Download
categories: keylogger, free keylogger, best free keylogger, windows monitoring, parental control |
 |
|
Best Free Keylogger Pro 7.2.0 download by bestxsoftware
... can monitor specific users, specific applications during specific time periods. You can also configure Best Free Keylogger to uninstall automatically on a specific date without being detected to the user. Parental controls ...
type: Shareware ($39.00)
View Details
Download
categories: keylogger, free keylogger, best free keylogger, windows monitoring, parental control |
 |
|
Data Destroyer 17.07 download by Hermetic Systems
When Windows 'deletes' a file it does not actually destroy the contents of the file but rather simply unlinks the file from the file directory system, leaving the contents of the file ...
type: Shareware ($27.95)
View Details
Download
categories: data destroyer, disk, purge, file purge, secure deletion, secure file deletion, sanitize, sanitization, DoD, Defense, 5220.22-M, file deletion |
 |
|
Desktop Patrol 2.1.2 download by Hkeylocal Executables
... per user basis Blocks users from saving email file attachments Custom entries can be added for desired monitoring of program and feature access Records the date/time and user name of users logging in/out of ...
type: Freeware
View Details
Download
categories: Desktop Protection, Desktop Lockdown, Desktop Security, Protection, Security, Lockdown |
 |
|
Action1 Local Users and Groups Analyzer 2.6 download by Action1 Corporation
... or IIS running? - List of endpoints exposing file shares to ransomware. - Show endpoints with remote ... any of your endpoints. - Users storing sensitive files locally on unsecured laptops. - Systems at risk ...
type: Freeware
View Details
Download
categories: local users and groups, member of Administrators group, enabled local accounts, disable Guest account, monitor account lockouts, who is logged in |
 |
|
Windows Credentials Viewer 1.0.0.7 download by Secured Globe Inc.
... help you retrieve the credentials you stored over time in Firefox, Chrome or Internet Explorer. Sports an ... the browser, site, users, password and the last date when it was accessed. View and copy passwords ...
type: Demo ($29.00)
View Details
Download
categories: credentials viewer, password reveler, restore passwords, stored passwords, stored credentials, Secured Globe, haephrati, Michael Haephrati, Ruth Haephrati, מיכאל האפרתי, רות האפרתי |
 |
|
Action1 Windows Configuration Reporting 2.6 download by Action1 Corporation
... or IIS running? - List of endpoints exposing file shares to ransomware. - Show endpoints with remote ... any of your endpoints. - Users storing sensitive files locally on unsecured laptops. - Systems at risk ...
type: Freeware
View Details
Download
categories: msinfo32, review OS configuration, misconfigured operating system, search event log data, Windows event log, list GPOs applied to computer |
 |