Related Keywords
256 bit encryption downloads256 bit aes encryption downloads
256 bit downloads
bit encryption downloads
128 bit encryption downloads
aes 256 bit downloads
serpent 256 bit downloads
aes 256 bit key downloads
software 256 bit downloads
crack 128 bit encryption pdf downloads
256 x 256 downloads
bit to bit downloads
256 downloads
256 aes downloads
256 colors downloads
256 compact flash downloads
256 chars limit downloads
256 bits downloads
bit downloads
bit torrent downloads
Top Software Keywords
decrypt downloadsencryption downloads
aes downloads
encryption software downloads
safe downloads
decryption downloads
file encryption downloads
privacy downloads
data encryption downloads
secure downloads
folder lock downloads
password downloads
security downloads
files downloads
recovery downloads
encrypt downloads
protection downloads
file downloads
email downloads
protect downloads
folder downloads
crack downloads
hide downloads
blowfish downloads
folders downloads
lock downloads
lock folder downloads
recover downloads
rijndael downloads
des downloads
Vista Download
Vista downloadVista antivirus download
Vista wallpaper download
Vista wallpapers download
Vista themes download
Vista pack download
Vista ultimate download
Vista home download
Vista basic download
Vista business download
Vista x64 download
Vista transformation download
Vista transformation pack download
Vista boot download
Vista dvd download
Vista sidebar download
Vista aero download
Vista product key download
Top Downloads
Top Rated
Navigation: Home
\ Security & Privacy
\ Encryption Tools \ GhostVolt Business Edition
GhostVolt Business Edition1.3.3.0 by GhostVolt |

|
Software Description:
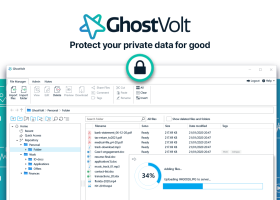
GhostVolt uses enterprise level AES encryption to keep your data secured at rest and in transit, taking care of encryption at every point, automatically. Zero back doors, you can be sure your data is invisible to bad actors that are practicing industrial espionage and theft of intellectual property. GhostVolt enables you to protect your business from privacy breaches and the cost of repairing the damage of a breach. Team based file sharing. ...
type: Demo ($85.00)
Download GhostVolt Business Editioncategories: anti-ransomware, encryption, security, privacy, collaboration, Data privacy, File encryption, file-sharing, Data control, HIPPA Add to Download Basket Report virus or spyware |
 [ Zoom screenshot ] |
|
| Software Info | |
|
Best Vista Download periodically updates pricing and software information of GhostVolt Business Edition full version from the publisher,
but some information may be out-of-date. You should confirm all information. Software piracy is theft, using crack, warez passwords, patches, serial numbers, registration codes, key generator, keymaker or keygen for GhostVolt Business Edition license key is illegal and prevent future development of GhostVolt Business Edition. Download links are directly from our mirrors or publisher's website, GhostVolt Business Edition torrent files or shared files from rapidshare, yousendit or megaupload are not allowed! |
|
| Released: | March 01, 2022 |
| Filesize: | 14.84 MB |
| Language: | English, French, German, Italian, Portuguese, Spanish |
| Platform: | Win2000, Windows XP, Windows 7 x32, Windows 7 x64, Windows 8, Windows 10, WinServer, WinOther, Windows Vista, Windows Vista x64 |
| Requirements: | Windows 11, 10, 8, Server 2012+ Processor speed 2Ghz or higher RAM 4 GB or higher Microsoft .NET 4.7 |
| Install | Install and Uninstall |
| Add Your Review or Windows Vista Compatibility Report |
GhostVolt Business Edition- Releases History |
| Software: | GhostVolt Business Edition 1.3.3.0 |
| Date Released: | Mar 1, 2022 |
| Status: | Major Update |
| Release Notes: | GhostVolt for Business features: User management Secure file collaboration Asset and user restrictions Detailed auditing and reporting Customizable policies File and user history evens Meet regulatory compliance and legislation (HIPPA, GDPR) Higher priority for support MS OneDrive support |
Most popular 256 bit encryption in Encryption Tools downloads for Vista |
|
Hash Codes 1.62.780.7200 download by Marek Sienczak
Hash Codes is a simple and easy to use application designed to enable users to hash data from keyboard, file or CD/DVD. This tool supports: Adler32, CRC32, CRC64, MD2, MD4, MD5, ...
View Details
Download
|
 |
|
EaseFilter Folder Locker 5.6.1.1 download by EaseFilter Inc.
... driver, file access control filter driver, transparent file encryption filter driver, process filter driver and registry filter ... Security SDK encompasses file security, digital rights management, encryption, file monitoring, file auditing, file tracking, data loss ...
type: Freeware
View Details
Download
categories: folder locker, file locker, access control, file encryption, secure file sharing, file access rights, file access, file control, file read, file write, file rename, file change, digital rights |
 |
|
DiskEncryptor 1.8 download by KernSafe Technology
A transparent(on-the-fly) disk/cd encryption system, which combin with AES 256-bit encryption. DiskEncryptor can make a disk partition encrypted on ... disk, when read and write, the decryption and encryption engine is running at background and transparently. DiskEncryptor ...
type: Freeware
View Details
Download
categories: encryption, disk encryption, cd encrypt, cd password, cd protect, disk encrypt, virtual disk, emulator |
 |
|
Kruptos 2 Professional 4.0.0.0 download by Kruptos 2 Software
... or any other file using proven and unbroken 256-bit encryption. There are no complex options or settings. Once ...
type: Shareware ($34.99)
View Details
Download
categories: File encryption, Decryption, Lock, encrypt, decrypt, security, blowfish, password protect, lock folder |
 |
|
Hash Codes x64 1.62.780.7200 download by Marek Sienczak
Hash Codes x64 is a simple and easy to use application designed to enable users to hash data from keyboard, file or CD/DVD. This tool supports: Adler32, CRC32, CRC64, MD2, MD4, ...
type: Open Source
View Details
Download
categories: x64 hash data, x64 encrypt data, x64 data encryption, x64 hash, x64 encrypt, x64 encryption |
 |
|
Protectorion ToGo 4.0.0.83 download by Braincell GmbH
... are unprotected from misuse. Protectorion ToGo features on-the-fly encryption with AES 256 bit, access encrypted data and passwords from any Windows ...
View Details
Download
|
 |
|
east-tec SafeBit 2.1 download by East-Tec
... need for your privacy. It features on-the-fly AES encryption, by creating virtual encrypted disk drives, where you ... case these fail. Nothing can crack the strong 256-bit AES encryption the program uses (selected by the ...
type: Shareware ($49.95)
View Details
Download
categories: safebit, disk encryption, drive encryption, hide, folder, encryption, software, disk, file, data, 256, aes, rijndael, password, protect, folder, protect, password, computer, strong, file, protect, virtual, disk, security, electronic, safe, esafe, privacy, data, encrypted |
 |
|
Paranoia Text Encryption for PC 15.0.4 download by Paranoia Works
... all unwanted readers. Texts are encrypted using strong encryption algorithms: AES (Rijndael) 256bits, RC6 256bit, Serpent 256bit, ... steganogram (JPEG image). Fully compatible with Paranoia Text Encryption for iOS (iPhone/iPad/iPod) and Secret Space Encryptor for ...
type: Freeware
View Details
Download
categories: encryption, encrypter, encryptor, encrypt, note, notes, text, texts, messages, chat, email, emails, sms, social, ciphering, encipher, aes, blowfish, threefish, serpent, 256, 512, 1024, bit, bits, steganography, JPG, cryptocurrency, seed, mnemonic, key, keys, safe, vault, password |
 |
|
Touch N Go 1.0.61228.0 download by BAYOMETRIC
... including Secure Sockets Layer (SSL) for data transfer, 256-bit Advanced Encryption Standard (AES) encryption, network configuration, and application-level controls. It uses FBI ...
View Details
Download
|
 |
|
Confidential Free Edition 1.0 download by Eagle-Soft
... a visible image. Confidential uses the AES-256 bits encryption algorithm as well as other security measures. Moreover, the presence of the hidden data is undetectable. Confidential can be executed from ...
View Details
Download
|
 |